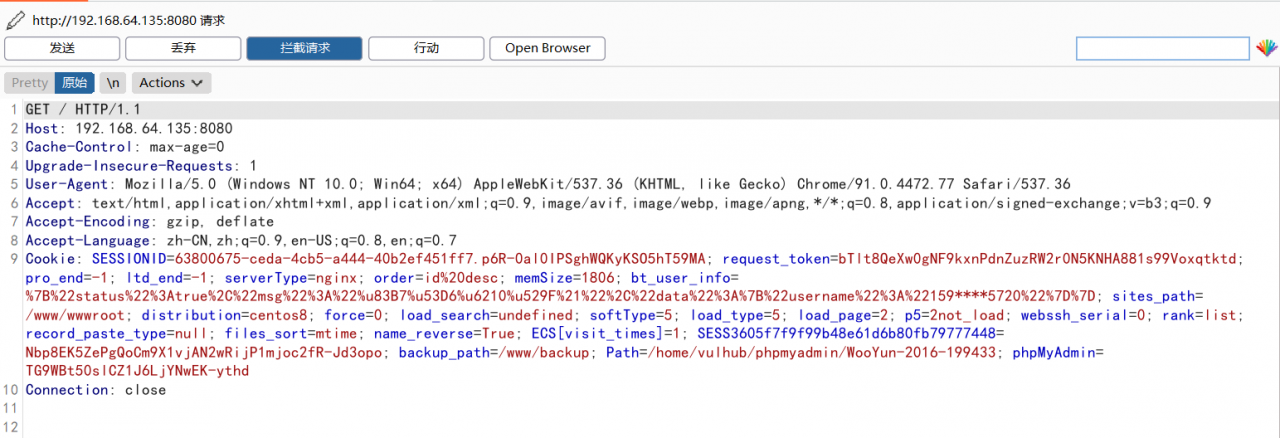
Docker compose reports an error and multiple containers conflict
When the vulnerability repeats, I want to open the vulnerability environment. The docker compose result reports an error. I understand that it is a multi container conflict problem
The error contents are as follows:
WARNING: Found orphan containers (unacc_slave_1, unacc_master_1) for this project. If you removed or renamed this service in your compose file, you can run this command with the --remove-orphans flag to clean it up.
unacc_web_1 is up-to-date
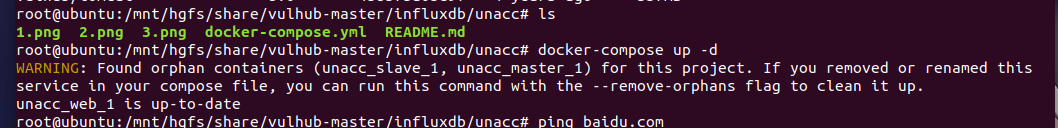
The solution given by the system here is: – remove orphans, but it will directly delete the container, which is obviously not very good
Learned that each configuration has a project name. If you provide the - P flag, you can specify the project name. If no flag is specified, compose uses the current directory name.
Use the following command to specify a container name
docker-compose -p xxx up -d
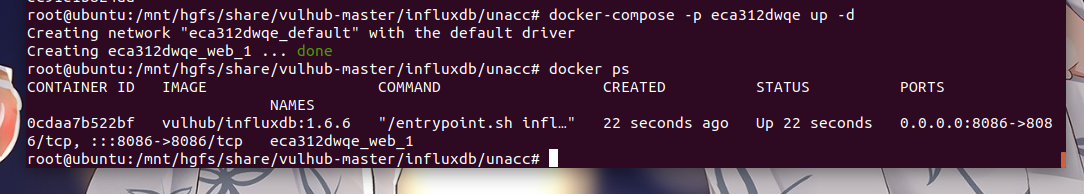
Open the 8086 port specified here in the container to successfully open the mirror environment.