Base64 coding is a kind of coding method of “guard against gentleman but not villain”. It is widely used in MIME Protocol. As the transmission code of e-mail, the generated code is reversible. The last two bits may have “=”, and the generated codes are all ASCII characters.
Advantages: fast speed, ASCII characters, incomprehensible to the naked eye
disadvantages: the encoding is relatively long, very easy to crack, only suitable for the occasion of encrypting non key information
Base64 encoding and decoding in Python
& gt; & gt; & gt; import Base64
& gt; & gt; s =’I am a string ‘
& gt; & gt; a = Base64. B64encode (s)
& gt; & gt; & gt; Print a
ztlkx9fwt / u0rg = =
& gt; & gt; & gt; print Base64. B64decode (a)
I am a string
Tag Archives: encryption
Visual Studio 2005 — Error code 1603 for this component means “Fatal error during installation.
Visual Studio 2005 — Error code 1603 for this component means “Fatal error during installation.
These days, because a project needs and want to install VS2005, Do not know how to return a responsibility, install to Microsoft Document Explorer 2005 prompt installation failure, how also continue not to go down, looked up a lot of data on the Internet, tried a lot of methods did not solve, on the difference reinstall the system, ha ha. In the last ready to give up suddenly because of a Qihoo 360 accidental system vulnerability repair installation failed to think of the reason, and then try, always successfully installed!
Now on the Internet on the installation of VS2005 Microsoft Document Explorer 2005 installation failure reasons and their own experience experience summary, previous lessons, hope to help others:
Before you start, please make sure that you have carefully reviewed the installation instructions of MS and tried the method. The official documentation is still very important.
The first recruit:
1. Empty all previous installations (including components from all previous versions), including the contents of the Windows /temp folder. 2. Open a vs cd-rom, have a file of Windows granted entry into the vs/wcu/msi31 folder, and install it. 3. Restart the computer and close the anti-virus software and firewall. 4. Modify the programe file and temp folders so that the programe program has sufficient permissions — in fact, you can login in and install 2005 with administrator.
5, now you can directly install.
(If this doesn’t work, see below)
The second recruit:
1. Open the VS2005 installation disk and enter the directory VS/WCU /DExplore
2. Manually run DExplorer. Exe
3. Run the VS2005 installation program again.
Three recruit:
1. Fix the.NET Framework 2.0
2. Remove a file named rgstrtn. LCK, which may be in
“%APPDATA%/Microsoft Help” or %temp% or directory under %temp% or
“/Documents and Settings/All Users{.windows}/Application Data/Microsoft Help”.
3, Then, see if ANY directories exist under “APPDATA%/Microsoft Help” or
“/Documents and Settings/All Users{Windows}/Application Data/Microsoft Help”, they need to be moved to another directory for this error to go away, a rename to another name will not work, The code is checking the Existance of ANY Directory of Name and the directories “APPDATA%/Microsoft Help” or “/Documents and Settings/All Users/Application Data/Microsoft Help” having ANY directory under it will not resolve this error.
All folders under Microsoft Help will be removed or renamed, pay attention to the path is good.
4. Ensure that you log in as Administrator and have sufficient permissions to operate the installation.
5. Install VS2005 again
(The above three tips are basically enough to solve most of these problems, if you are not good, you may be in the same situation as me, then try the following tips, hehe)
The fourth recruit:
1. Open your installer’s temp directory. Mine is /Documents and Settings/ Luocl (the username you logged in to) /Local Settings/ temp.
2. Remove the Temp folder’s encryption attribute: Click the Temp file’s attribute — & GT; Conventional – & gt; Advanced, uncheck the “encrypt Content to Protect Data” TAB, and click OK.
3. Reinstall VS2005.
Connection authorization failure occurred. Reason: local security service non retryable error solution
Study found that after is the system differences, the password can’t be in clear text mode is stored in the system, are saved after through the corresponding encryption algorithm, DB2 USES a SHA256 encryption, and a lot of high version of the Linux the default encryption algorithm is the SHA512, such system to create DB2 user password by SHA512 stored in the system, the connection to DB2 by SHA256 password passwords in encrypted and stored in the system, the result is, of course, failure, the solution is as follows:
Open the /etc/pam.d/system-auth file, find the second line of passwd configuration, change sha512 to Sha256, and save;
Rerun the passwd DB2 user and set the password;
Success;
This will replace the system encryption method with SHA256 and then update the saved password.
Java encrypts the string with MD5
for a plaintext, for security, sometimes we need to do MD5 encryption, the following provides a Java tool method, directly called.
/**
* MD5加密
*/
public class MD5Util {
/**
* Encodes a string 2 MD5
*
* @param str String to encode
* @return Encoded String
* @throws NoSuchAlgorithmException
*/
public static String crypt(String str) {
if (str == null || str.length() == 0) {
throw new IllegalArgumentException("String to encript cannot be null or zero length");
}
StringBuffer hexString = new StringBuffer();
try {
MessageDigest md = MessageDigest.getInstance("MD5");
md.update(str.getBytes());
byte[] hash = md.digest();
for (int i = 0; i < hash.length; i++) {
if ((0xff & hash[i]) < 0x10) {
hexString.append("0" + Integer.toHexString((0xFF & hash[i])));
} else {
hexString.append(Integer.toHexString(0xFF & hash[i]));
}
}
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
}
return hexString.toString();
}
}
JavaScript emoticon package encryption
- after reading this article you may feel that you know nothing about the power of JavaScript!
- let’s see what kind of encryption this is!
- is the author of the encryption: from Japan Yosuke HASEGAWA
- his project address: http://utf-8.jp/public/aaencode.html
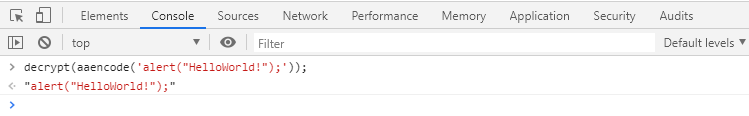
we encrypt a string of JS code with this method: alert(” HelloWorld! );
function aaencode( text ) { var t; var b = [ "(c^_^o)", "(゚Θ゚)", "((o^_^o) - (゚Θ゚))", "(o^_^o)", "(゚ー゚)", "((゚ー゚) + (゚Θ゚))", "((o^_^o) +(o^_^o))", "((゚ー゚) + (o^_^o))", "((゚ー゚) + (゚ー゚))", "((゚ー゚) + (゚ー゚) + (゚Θ゚))", "(゚Д゚) .゚ω゚ノ", "(゚Д゚) .゚Θ゚ノ", "(゚Д゚) ['c']", "(゚Д゚) .゚ー゚ノ", "(゚Д゚) .゚Д゚ノ", "(゚Д゚) [゚Θ゚]" ]; var r = "゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); "; if( /ひだまりスケッチ×(365|356)\s*来週も見てくださいね[!!]/.test( text ) ){ r += "X=_=3; "; r += "\r\n\r\n X/_/X < \"来週も見てくださいね!\";\r\n\r\n"; } r += "(゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);"+ "(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] "+ ",゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] "+ ",゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];"+ "(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];"+ "(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];"+ "(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + "+ "((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+"+ "((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+"+ "((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+"+ "((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];"+ "(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+"+ "((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+"+ "((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; "+ "(゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\\\'; "+ "(゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];"+ "(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];"+//TODO "(゚Д゚) [゚o゚]='\\\"';"+ "(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+"; r += "(゚Д゚)[゚o゚]+ "; for( var i = 0; i < text.length; i++ ){ n = text.charCodeAt( i ); t = "(゚Д゚)[゚ε゚]+"; if( n <= 127 ){ t += n.toString( 8 ).replace( /[0-7]/g, function(c){ return b[ c ] + "+ "; } ); }else{ var m = /[0-9a-f]{4}$/.exec( "000" + n.toString(16 ) )[0]; t += "(o゚ー゚o)+ " + m.replace( /[0-9a-f]/gi, function(c){ return b[ parseInt( c,16 ) ] + "+ "; } ); } r += t; } r += "(゚Д゚)[゚o゚]) (゚Θ゚)) ('_');"; return r; }yes we got a bunch of cute memes!!
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (o^_^o)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');however, these memes are not as cute as you might think, and they are just as damaging!!
his corresponding decryption method is
function decrypt (text) { var evalPreamble = "(\uFF9F\u0414\uFF9F) ['_'] ( (\uFF9F\u0414\uFF9F) ['_'] ("; var decodePreamble = "( (\uFF9F\u0414\uFF9F) ['_'] ("; var evalPostamble = ") (\uFF9F\u0398\uFF9F)) ('_');"; var decodePostamble = ") ());"; // strip beginning/ending space. text = text.replace(/^\s*/, "").replace(/\s*$/, ""); // returns empty text for empty input. if (/^\s*$/.test(text)) { return ""; } // check if it is encoded. if (text.lastIndexOf(evalPreamble) < 0) { throw new Error("Given code is not encoded as aaencode."); } if (text.lastIndexOf(evalPostamble) != text.length - evalPostamble.length) { throw new Error("Given code is not encoded as aaencode."); } var decodingScript = text.replace(evalPreamble, decodePreamble) .replace(evalPostamble, decodePostamble); return eval(decodingScript); }