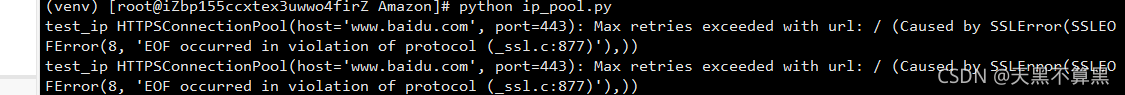
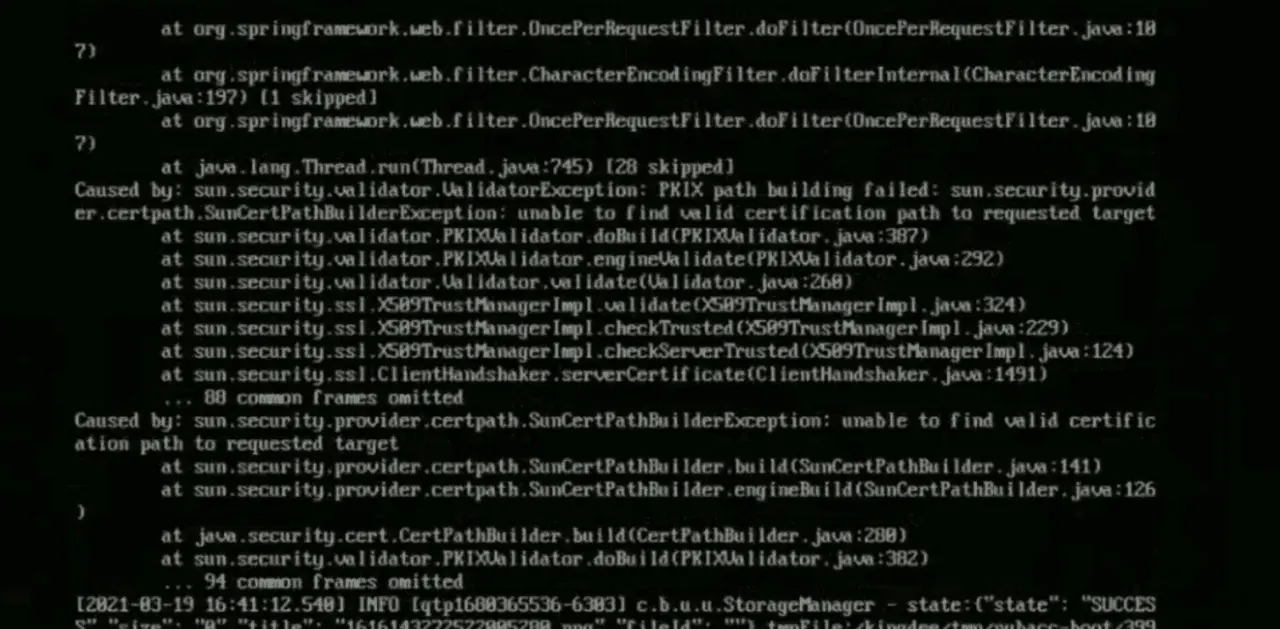
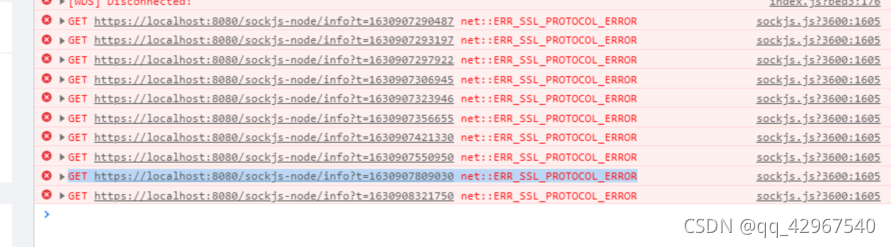
After the server restarts one day, Apache cannot start. Check the Apache error log:
cat /var/log/httpd/error_log
The following errors are found:
[Wed Aug 25 18:49:00.134257 2021] [:error] [pid 1607] SSL Library Error: -8181 Certificate has expired
[Wed Aug 25 18:49:00.134318 2021] [:error] [pid 1607] Unable to verify certificate 'Server-Cert'. Add "NSSEnforceValidCerts off" to nss.conf so the server can start until the problem can be resolved.
Use the following command to view the certificate information and find that the certificate has expired:
certutil -d /etc/httpd/alias -L -n Server-Cert
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4 (0x4)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: "CN=Certificate Shack,O=example.com,C=US"
Validity:
Not Before: Fri Jan 24 15:03:11 2017
Not After : Wed Jan 24 15:03:11 2021
You can use temporary methods to solve this problem:
first set the certificate inspection prohibition, and then cancel this setting after the certificate is updated. Operation method:
add the nssenforcevalidcerts off setting in the/etc/httpd/conf.d/nss.conf file to temporarily cancel the certificate inspection.
The permanent solution is to regenerate the certificate. The command is as follows:
yum install httpd mod_nss
certutil -d /etc/httpd/alias -L -n Server-Cert
cd /etc/httpd/alias
rm -f *.db
/usr/sbin/gencert /etc/httpd/alias > /etc/httpd/alias/install.log 2>&1
Then check that the certificate expiration date is normal.
certutil -d /etc/httpd/alias -L -n Server-Cert
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4 (0x4)
Signature Algorithm: PKCS #1 SHA-256 With RSA Encryption
Issuer: "CN=Certificate Shack,O=example.com,C=US"
Validity:
Not Before: Fri Aug 27 07:27:30 2021
Not After : Wed Aug 27 07:27:30 2025
Try to start Apache and find that it still can’t be started. Check the error log again and find a new error report:
[Fri Aug 27 15:38:17.483837 2021] [:error] [pid 15043] Server user apache lacks read access to NSS key database /etc/httpd/alias/key3.db.
It should be that the Apache user does not have permission to the key3.db file
let’s check the file attributes:
ls -l /etc/httpd/alias/
total 88
-rw-------. 1 root root 65536 Oct 26 17:26 cert8.db
-rw-------. 1 root root 5872 Oct 26 17:26 install.log
-rw-------. 1 root root 16384 Oct 26 17:26 key3.db
lrwxrwxrwx. 1 root root 24 Nov 15 10:58 libnssckbi.so -> /usr/lib64/libnssckbi.so
-rw-------. 1 root root 16384 Oct 26 17:26 secmod.db
Then modify the attributes of all DB files in the/etc/httpd/alias/Directory:
chown :apache /etc/httpd/alias/*.db
chmod u=rw,g=r *.db
The effect is the same with the following two commands:
chown root.apache /etc/httpd/alias/*.db
chmod 0640 /etc/httpd/alias/*.db
After modification, check the properties of the DB file:
ls -l /etc/httpd/alias/
total 88
-rw-r-----. 1 root apache 65536 Oct 26 17:26 cert8.db
-rw-------. 1 root root 5872 Oct 26 17:26 install.log
-rw-r-----. 1 root apache 16384 Oct 26 17:26 key3.db
lrwxrwxrwx. 1 root root 24 Nov 15 10:58 libnssckbi.so -> /usr/lib64/libnssckbi.so
-rw-r-----. 1 root apache 16384 Oct 26 17:26 secmod.db
Finally, start Apache:
systemctl start httpd
Start successfully!