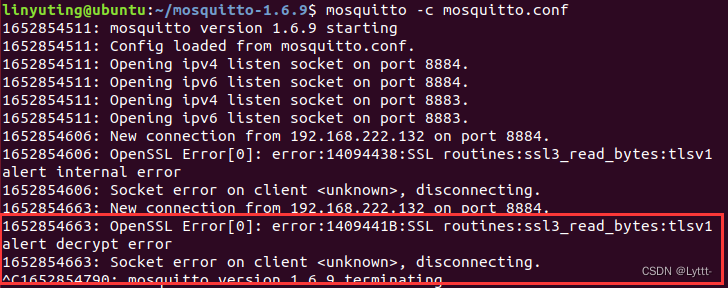
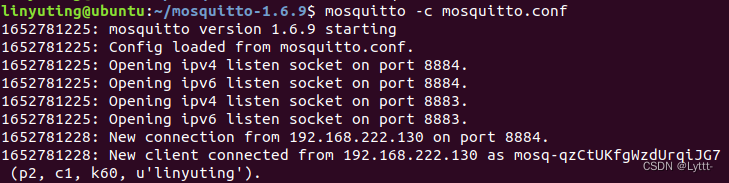
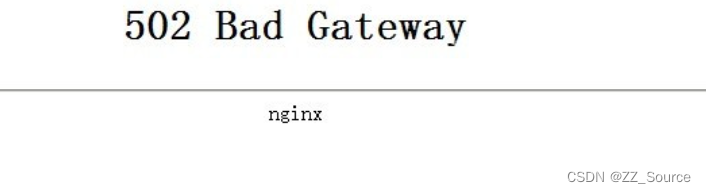
error:1035 connect() failed (111: Connection refused) while connecting to upstream, client: …217, server: .com, request: “POST /api/userLogin HTTP/1.1”, upstream: “http://.1:8443/userLogin”, host: “*.com”
1. Cause
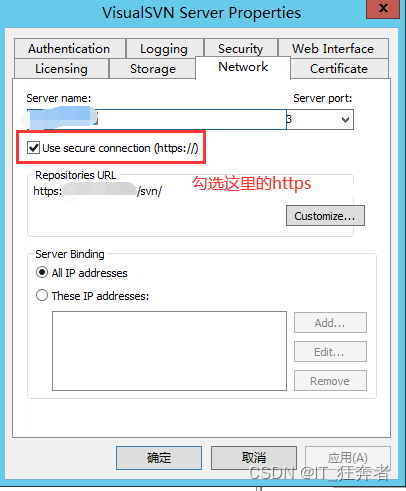
The deployment of the project is on Tencent cloud server, http upgraded to https, using Tencent ssl certificate, Ali’s domain name, during the nginx.conf configuration process, there is a front-end to back-end send request failure problem. The following error occurs.
The nginx.conf configuration is as follows:
server{
#SSL The default access port number is 443
listen 443 ssl;
server_name domain;
default_type text/html;
ssl_certificate certificate file path (.crt/.pem);
ssl_certificate_key private key file path (.key);
ssl_session_timeout 5m;
# Please configure according to the following protocols
ssl_protocols TLSv1.2 TLSv1.3;
s#Please configure the encryption suite according to the following suite configuration, written following the openssl standard.
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
location/{
root /usr/share/nginx/html/dist/;
try_files $uri $uri/ /index.html;
index index.html;
}
location /api/ {
default_type application/json;
proxy_pass http://localhost:8443/;
}
}
2. Solutions
Add a clause to the nginx.conf configuration: proxy_set_header Host $http_host;
server{
#SSL The default access port number is 443
listen 443 ssl;
server_name domain;
default_type text/html;
ssl_certificate certificate file path (.crt/.pem);
ssl_certificate_key private key file path (.key);
ssl_session_timeout 5m;
# Please configure according to the following protocols
ssl_protocols TLSv1.2 TLSv1.3;
s#Please configure the encryption suite according to the following suite configuration, written following the openssl standard.
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
location/{
root /usr/share/nginx/html/dist/;
try_files $uri $uri/ /index.html;
index index.html;
}
location /api/ {
# nginx reverse proxy rewrites the host field attribute in the request header
proxy_set_header Host $http_host;
default_type application/json;
proxy_pass http://localhost:8443/;
}
}