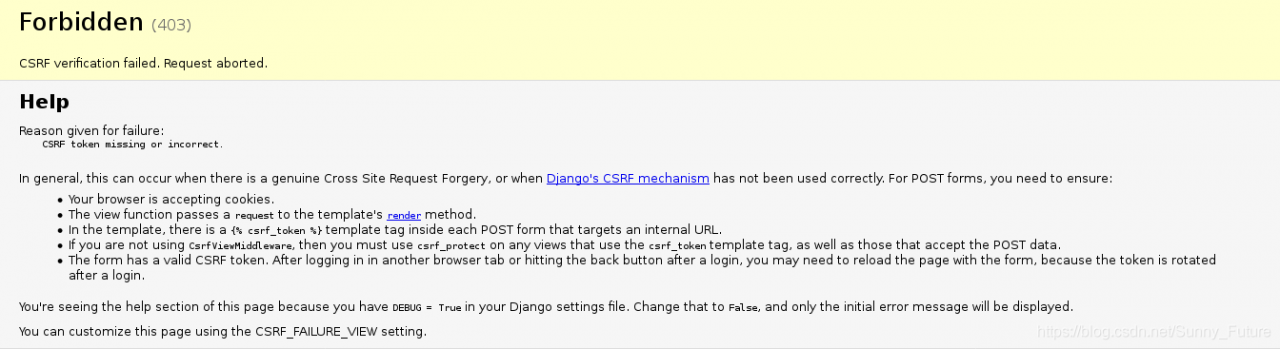
Forbidden (403)
CSRF验证失败。请求中止。
Help
Reason given for failure:
CSRF token missing or incorrect.
In general, this can occur when there is a genuine Cross Site Request Forgery, or when Django's CSRF mechanism has not been used correctly. For POST forms, you need to ensure:
Your browser is accepting cookies.
The view function passes a request to the template's render method.
In the template, there is a {% csrf_token %} template tag inside each POST form that targets an internal URL.
If you are not using CsrfViewMiddleware, then you must use csrf_protect on any views that use the csrf_token template tag, as well as those that accept the POST data.
The form has a valid CSRF token. After logging in in another browser tab or hitting the back button after a login, you may need to reload the page with the form, because the token is rotated after a login.
You're seeing the help section of this page because you have DEBUG = True in your Django settings file. Change that to False, and only the initial error message will be displayed.
You can customize this page using the CSRF_FAILURE_VIEW setting.
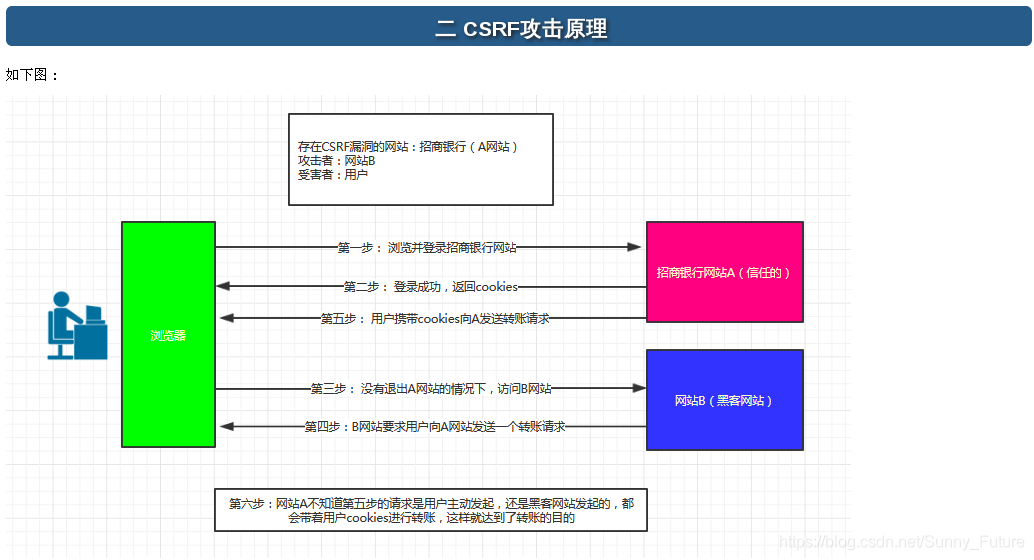
 ** cross-site Request Forgery (CSRF) vulnerability. ** is a malicious exploit of a website. Although it sounds like cross-site scripting (XSS), it is very different from XSS, which exploits a trusted user within a site, while CSRF exploits a trusted site by impersonating a Request from a trusted user. CSRF attacks tend to be less prevalent (and therefore have relatively few resources to defend against) and harder to defend against than XSS attacks, and are therefore considered more dangerous than XSS attacks
** cross-site Request Forgery (CSRF) vulnerability. ** is a malicious exploit of a website. Although it sounds like cross-site scripting (XSS), it is very different from XSS, which exploits a trusted user within a site, while CSRF exploits a trusted site by impersonating a Request from a trusted user. CSRF attacks tend to be less prevalent (and therefore have relatively few resources to defend against) and harder to defend against than XSS attacks, and are therefore considered more dangerous than XSS attacks
can understand :
the attacker steal your identity, in the name of your sending malicious request, the request for server is perfectly legal, but finished the attacker’s expectation of an operation, such as in the name of your email, send messages, to steal your account, add a system administrator, or even to buy goods, virtual currency transfer, etc.
Django’s protection against CSRF is to place an auto-generated token in each generated form to determine whether a POST request is coming from the same site
solution one:
Use the Django template here. Use the TemplateTag to add CSRF tokens. Add {% crrf_token %}
in the from form
# index.html
...
<form method="post">
<div >
<input name="username" placeholder="username"><br>
<input name="password" placeholder="password"><br>
<div >
<button type='submit' id='btn'>提交</button>
</div>
</div>
{% csrf_token %}
</form>
...
again, refresh the page and resubmit the form to access
normally
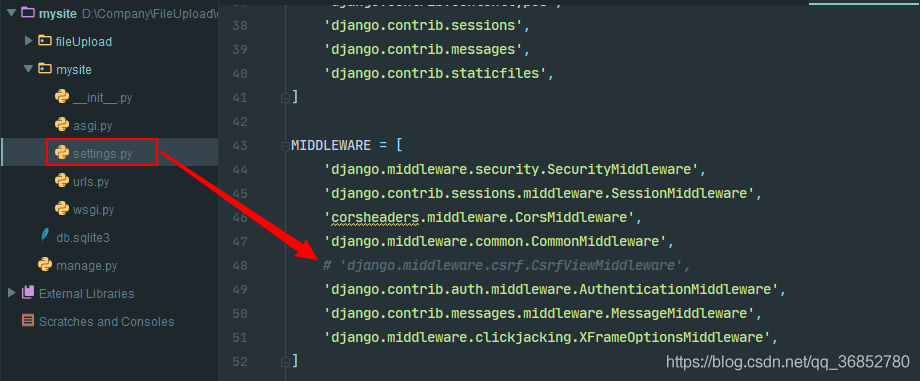
solution two:
simply ignores this check and comments CSRF in the Settings. Py of the project
MIDDLEWARE = [
'django.middleware.security.SecurityMiddleware',
'django.contrib.sessions.middleware.SessionMiddleware',
'django.middleware.common.CommonMiddleware',
#'django.middleware.csrf.CsrfViewMiddleware',
'django.contrib.auth.middleware.AuthenticationMiddleware',
'django.contrib.messages.middleware.MessageMiddleware',
'django.middleware.clickjacking.XFrameOptionsMiddleware',
]
CSRF (cross-site request forgery)
CSRF specific see:
https://www.cnblogs.com/liuqingzheng/p/9505044.html
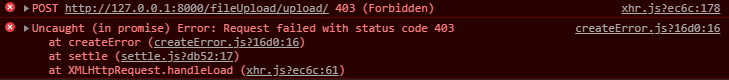
 is not recommended
is not recommended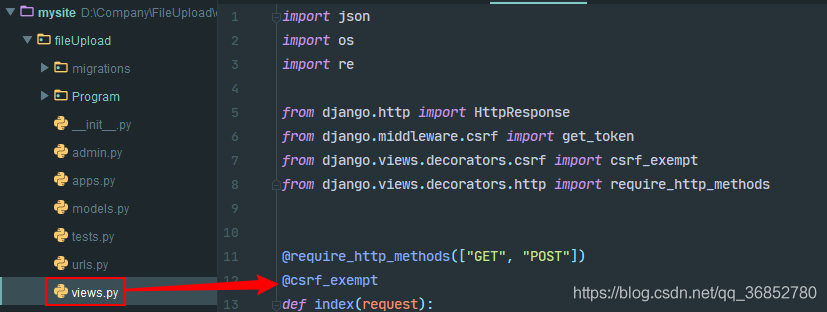 to the interface view
to the interface view ** cross-site Request Forgery (CSRF) vulnerability. ** is a malicious exploit of a website. Although it sounds like cross-site scripting (XSS), it is very different from XSS, which exploits a trusted user within a site, while CSRF exploits a trusted site by impersonating a Request from a trusted user. CSRF attacks tend to be less prevalent (and therefore have relatively few resources to defend against) and harder to defend against than XSS attacks, and are therefore considered more dangerous than XSS attacks
** cross-site Request Forgery (CSRF) vulnerability. ** is a malicious exploit of a website. Although it sounds like cross-site scripting (XSS), it is very different from XSS, which exploits a trusted user within a site, while CSRF exploits a trusted site by impersonating a Request from a trusted user. CSRF attacks tend to be less prevalent (and therefore have relatively few resources to defend against) and harder to defend against than XSS attacks, and are therefore considered more dangerous than XSS attacks 