Causes of loopholes
Normally, you can access/article and enter a numeric ID to get the article content. However, if a spel expression is passed in, you will go to the error page and parse the spel expression content and reflect it in the error page.
Debug process
Similarly, starting from the dispatcherservlet.Dodispatch() function, we quickly located the key class: propertyplaceholderhelper class
in dispatcherservlet, an error is reported due to the following judgment:
protected void doDispatch(HttpServletRequest request, HttpServletResponse response) throws Exception {
...
if (asyncManager.isConcurrentHandlingStarted()) {
return;
}
...
}
The error content is numberformatexception, which converts the entered value into a digital error.
First look at the propertyplaceholderhelper.Parsestringvalue() method
rotected String parseStringValue(String strVal, PropertyPlaceholderHelper.PlaceholderResolver placeholderResolver, Set<String> visitedPlaceholders) {
StringBuilder result = new StringBuilder(strVal);
int startIndex = strVal.indexOf(this.placeholderPrefix);
while(startIndex != -1) {
int endIndex = this.findPlaceholderEndIndex(result, startIndex);
if (endIndex != -1) {
String placeholder = result.substring(startIndex + this.placeholderPrefix.length(), endIndex);
String originalPlaceholder = placeholder;
if (!visitedPlaceholders.add(placeholder)) {
throw new IllegalArgumentException("Circular placeholder reference '" + placeholder + "' in property definitions");
}
placeholder = this.parseStringValue(placeholder, placeholderResolver, visitedPlaceholders);
//Here
String propVal = placeholderResolver.resolvePlaceholder(placeholder);
if (propVal == null && this.valueSeparator != null) {
int separatorIndex = placeholder.indexOf(this.valueSeparator);
if (separatorIndex != -1) {
String actualPlaceholder = placeholder.substring(0, separatorIndex);
String defaultValue = placeholder.substring(separatorIndex + this.valueSeparator.length());
propVal = placeholderResolver.resolvePlaceholder(actualPlaceholder);
if (propVal == null) {
propVal = defaultValue;
}
}
}
......
}
return result.toString();
}
After that, it will return to the view, which contains ${timestamp}, ${error}, ${status}, and ${message}. The view will judge whether the value starts with “${” through circular traversal
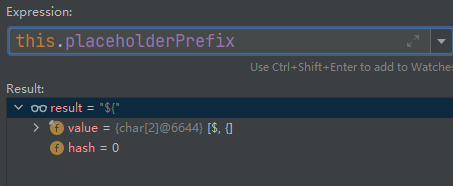
As long as it starts with “${“, it will enter the spel expression execution stage. However, when we set the value of message to payload, which also starts with “${“, it will also execute payload. It does not verify the value of controllable parameter message.
After that, use the errormvcautoconfiguration.Resolveplaceholder() method to parse the spel expression and get the value.
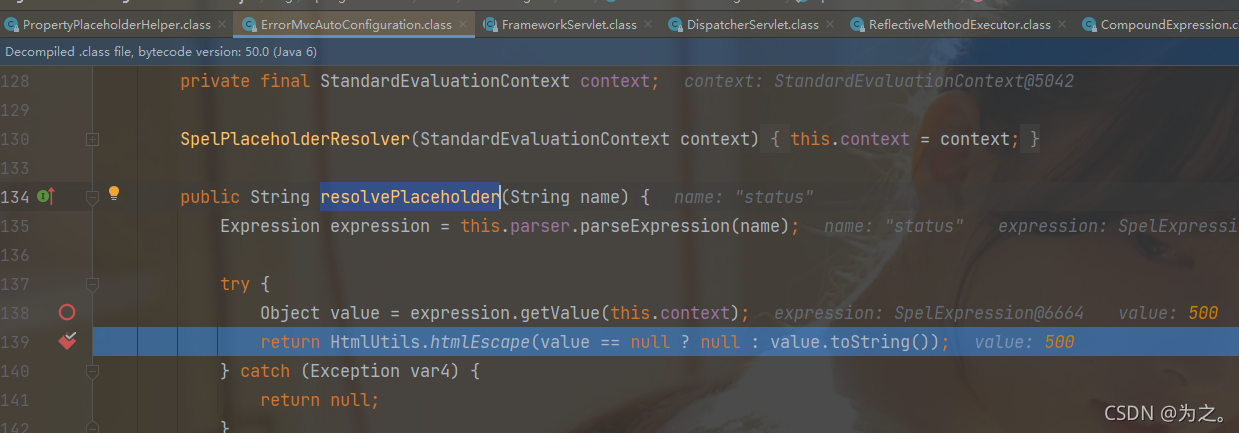
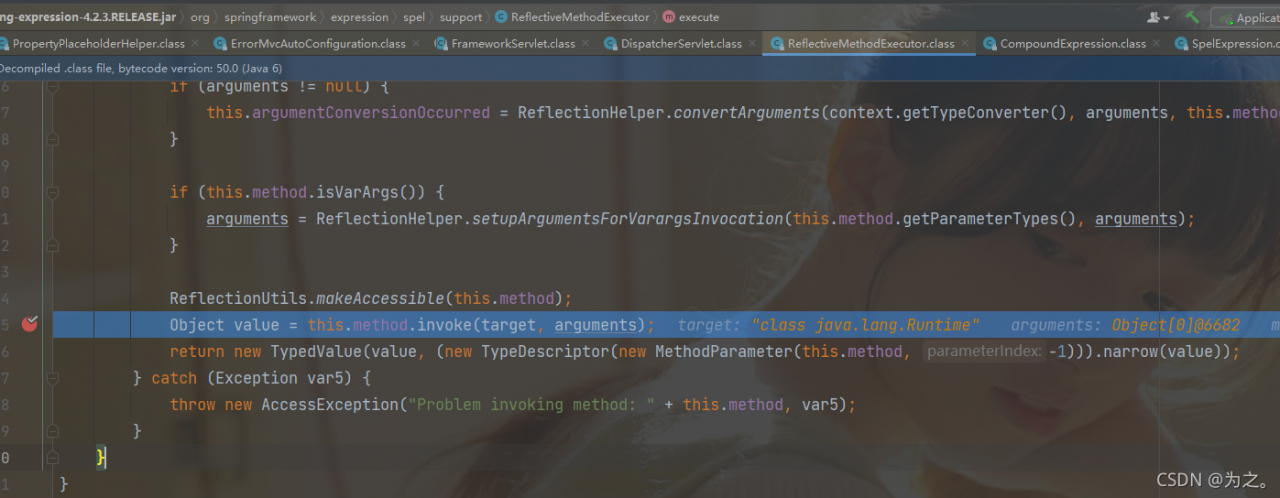
this step is to get the value of status. When the payload is reached, it will be parsed into the runtime class and execute the exec method. This step is to get the runtime instance through reflection.
Summary
Because the value passed in will determine whether it is a number, if it is not a number, an error will be reported and you will enter the error page. The error page contains some spel expressions, so the spel expressions in the error page will be searched and parsed in a loop, and finally rendered to the page. However, the reason for the problem is ${messgae} If the value of is also a spel expression, it will continue to parse the expression circularly, so as to achieve command injection, that is, the user-controllable parameters are not verified.
Repair suggestions
The reason is that the ID is not filtered in the spel direction. Therefore, I summarize and suggest the following points:
- filter IDS, set black-and-white lists, filter values such as ${, upgrade the Framework version, patch, and customize the error page
Read More:
- [Solved] Springboot loads static page Error: whitelabel error page
- SpringBoot Project Run Page Error: Whitelabel Error Page This application has no explicit mapping for /error
- SpringBoot: Whitelabel Error Page 404 [How to Solve]
- Springboot reports an error whitelabel error page
- SpringBoot 404 Error: Whitelabel Error Page This application has no explicit mapping for /error, so yo
- H2 memory database Oracle mode page error: rg.springframework.dao.InvalidDataAccessResourceUsageException: could not prepar
- [Solved] JPA query data error: Page 1 of 0 containing UNKNOWN instances
- thymeleaf Error: An error happened during template parsing Cannot render error page for request
- NULL value exception occurs when freemarker renders the page globally in the springboot project
- Android startup page (solve the problem of starting black and white screen)
- Spring boot real time HTML page
- Ternary operator in Java?: error: not a statement
- How to Solve Tomcat Error: Could not resolve view with name ‘xxx/xxxxxxx‘ in servlet with
- Upload file error analysis standardmultiparthttpservletrequest
- JPA multiple-data source startup error: org.springframework.beans.factory.BeanCreationException: Error creating bean with name ‘t
- [Solved] asList().add() error: UnsupportedOperationException
- [Solved] Circular view path [index]: would dispatch back to the current handler URL [] again. Che
- How to Solve mybatis-plus Paging Plug-in PaginationInnerInterceptor error
- JAVA: How to Delete the Last Bit of String
- I/O error while reading input message; nested exception is java.io.IOException: Stream closed