There are many articles on role-based authorization strategy. Here are some special points.
1. Differences among global roles, item roles and node roles
Since it is role-based permission control, Jenkins naturally defines a variety of roles to control permissions from the perspective of roles. Among them,
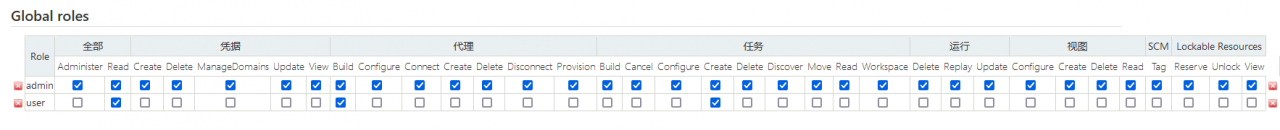
Global roles: global roles, such as admin, job creator, anonymous, etc. set permissions for all, credentials, agents, tasks, runs, views, SCM, and lockable resources from a global perspective.
Item roles: create an item role, which allows you to grant job and run permissions from the perspective of the item.

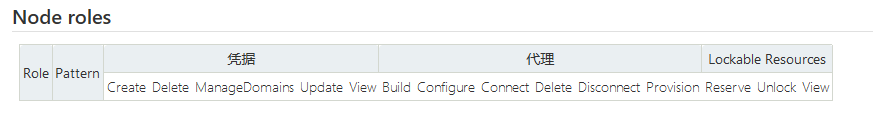
Node roles: create a proxy role that allows you to set node related permissions.
The configuration in global roles acts on all items in Jenkins and overrides the configuration in items roles. If you assign the job read permission under global roles to a role, this role allows you to read all jobs, no matter how you set it in project roles.
2. Several points for attention
1) All non admin roles must be given global read permission in a global role.
2) Permission to create job item: the job create permission in global roles must be assigned to this role.
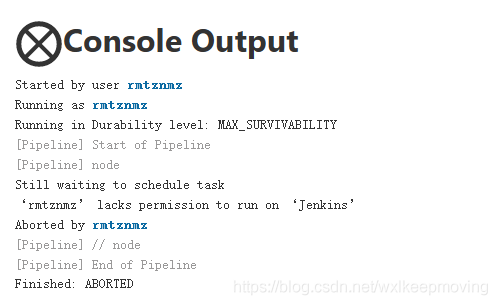
Selecting create item permission only in item roles does not work. Because creating an item is a global function, after creating an item, determine which role management role it belongs to according to the regular expression.
Otherwise, an error will be reported: Lakes permission to run on ‘Jenkins’
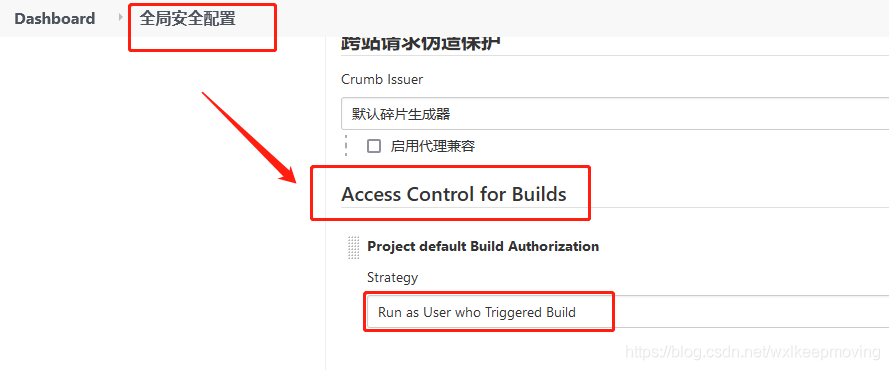
3) If run as user who triggered build is selected in the global security configuration, the agent build permission in the global roles must be assigned to the role.
Node roles have not been used yet, and will be added later.