Requests module has been normal, before one day began to HTTPS requests the thrown error:
requests. Exceptions. SSLError: [1] Errno _ssl. C: 504: error: 14090086: SSL routines: SSL3_GET_SERVER_CERTIFICATE: certificate verify failed
At first, I thought the agent was unstable and restarting the agent was invalid, then I restarted the machine and it was invalid. Code problems?It is ok to copy the error code to another machine, or to report the certificate error if the code running normally on another machine is copied to the error machine. Just try the requests. Get requests FOR HTTP.
All sorts of solutions have been tried in vain. Search the Internet for answers. I found two solutions: the first One I used. The second one is also backed up.
The first solution:
What is SSL validation?
SSL certificates are SSL protocol compliant, issued by a trusted digital certificate authority (CA) after server authentication, with server authentication and data transmission encryption.
SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed
add a new feature in python 2.7 that will validate the SSL certificate when urlopen requests it, or make an error if it is a self-signed SSL certificate.
Python request SSL error
has a verify parameter in both the request-post and request-get methods. Set the verify parameter to FALSE.
r = requests. Get (“xxx.com”, headers=request_headers, verify=False)
print r.tent
The second solution:
Try:
sudo apt-get install ca-certificates
sudo update-ca-certificates
No effect,
finally tried the following one that worked:
sudo pip uninstall -y certifi
sudo pip install certifi==2015.04.28
Of course, there are caveats:
/usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/util/ssl_.py:79: InsecurePlatformWarning: A true SSLContext object is not available. This prevents urllib3 from configuring SSL appropriately and may cause certain SSL connections to fail. For more information, see https://urllib3.readthedocs.org/en/latest/security.html#insecureplatformwarning.
InsecurePlatformWarning
No, at least we can use it for now. The reason for this is estimated to be that the Later version (2016.2.8) CertiFI is more certifying.
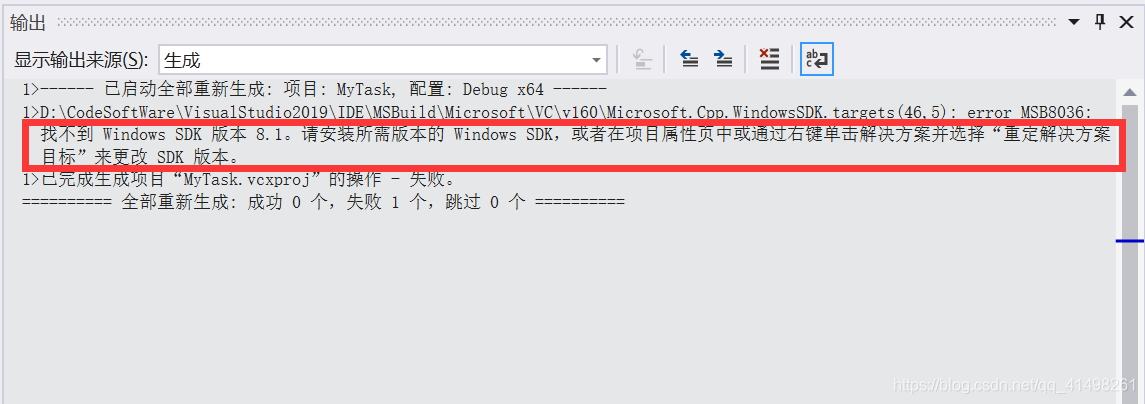
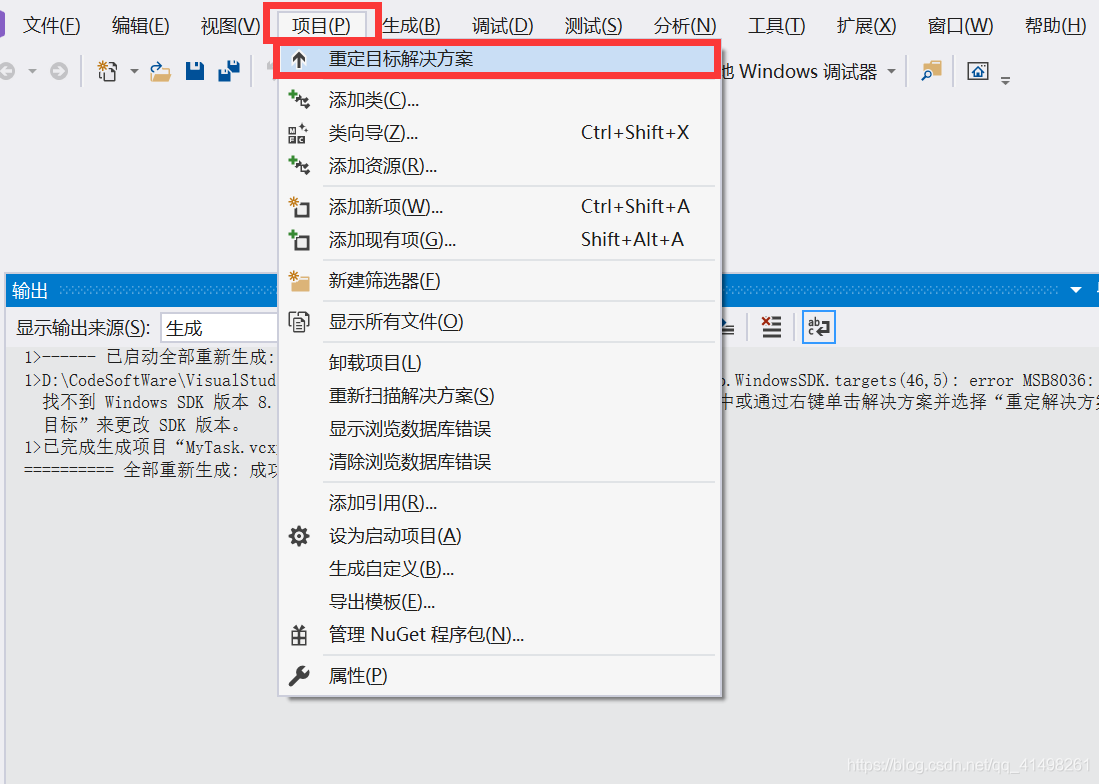 select the appropriate SDK version and platform toolset (general default)
select the appropriate SDK version and platform toolset (general default)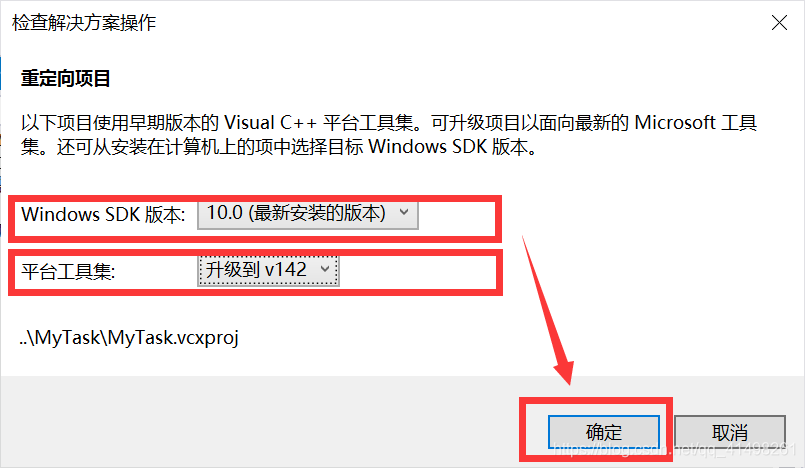
 rebuild solution
rebuild solution