
How to use STIX for Automated Sharing and Graphing of Cyber Threat Data
This article does not intend to carry out translation operation, only focuses on the main points and my personal views. The article is the clearest I have read recently, or the one I can understand best…
STIX Overview
STIX itself is a set of XML schemas which together comprise a language for describing cyber threat information in a standardized manner. This is important because cyber threat sharing currently occurs manually between trusted parties; with a standardized way of describing the data, automated threat sharing becomes possible. For this purpose MITRE has also developed TAXII to share STIX data over HTTP and HTTPS.
The concept of STIx/TAXII was proposed out of the existence of sharing. Threat intelligence varies from agency to agency, and if you want to share it, you have to have a set of standards that everyone can understand. On the other hand, the establishment of standards is conducive to the completion of machine-read, automatic analysis and storage . In general, standards are proposed for two purposes, much like protocols:
- Shared computer automation operation
If stix is regarded as a data structure, taxii is the transmission mode of these bombs. On haliataxii.com, only HTTP is transmitted, but this is only a demo test. Therefore, for security, taxii must be the world of HTTPS .
STIX Benefits
STIX can be used to characterize indicators, TTPs, exploit targets, and other aspects of a cyber threat. STIX takes advantage of another MITRE schema, CybOX, to represent Observables, and can be extended to utilize existing schemas, such as CAPEC or OpenIOC.
In STIX’s data structure, Obsevables USES CybOX to describe the appearance characteristics. But not the same as stix==Cybox. Different threat intelligence protocols need to be able to be converted, and many open source tools are also provided on github.
In fact, a lot of times, data processing USES json, which is concise and efficient. However, as for intelligence analysis, sometimes the data description is very complex, and using json is counterproductive, while XML has an advantage.
For more advanced applications, the framework corresponding to python, such as python-stix, is often used to describe the intelligence content, and the framework automatically completes the storage in XML format. If the user needs to interpret, use the corresponding method to read the data from the file. This avoids the complexity of manipulating XML manually.
STIX can also be converted to HTML with the use of an XSLT transform
All in all, the stix standard has been supported by the MITRE organization, as can be seen from the number of open source tools available on github. However, these frameworks are confirmatory demos, and the enterprise has a long way to go if it wants to implement them.
STIX Example
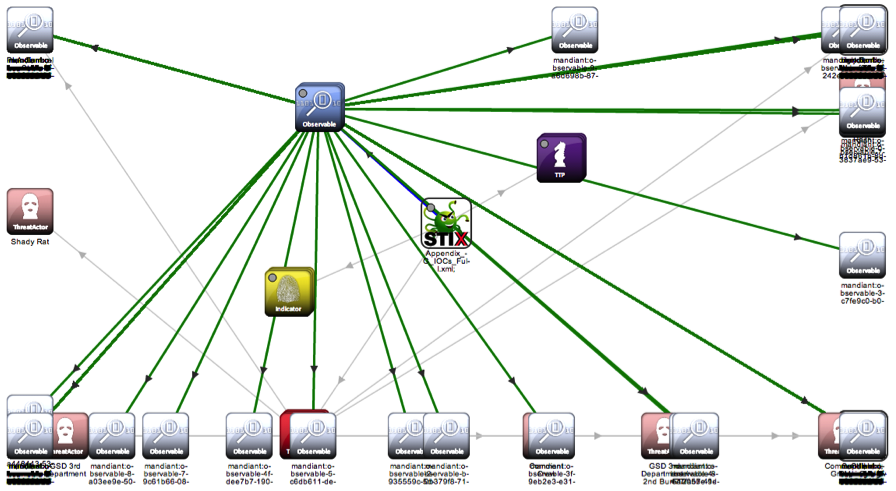
The figure above is implemented using stix-viz. The emergence of this tool is also inevitable. From the current trend, the emergence of visualization is necessary to help people interpret. The program exists on Github and is currently easy to install and ready to run with the JRE configured. Here is a joke, the author’s graph structure is not really good.
In my opinion, stix-viz is only the prototype at present, and there are many inconveniences in the operation process. For example, the text in the HTML version is too small and there are few options. But the visualization requirement is basically done.
STIX and Recorded Future
Give this title Recorded Future thumb up.
documenting the future is what all security threat intelligence is about.
By managing information security threat indicators in structured formats, like STIX, defenders can automate the process of finding connections between internal incidents and external sources. This can work bidirectionally: searching Recorded Future for more context around internally observed indicators, or testing trending indicators from open source reporting against internal datasets.
By analyzing the signs of threat, the threat harm can be avoided or mitigated. How do you do correlation analysis, that’s what stix does.
Look for signs from the inside, such as whether such behavior has occurred in the past, etc. Check with external threat intelligence to see if such information is available and if it is recorded in the knowledge base. Once the processing is complete, if it is a new threat, the intelligence needs to be eventually documented and Shared.