SSH Remote ulimit does not work
Problem description
The contents of the operating system/etc/security/limits.conf file are as follows:
* soft memlock unlimited
* hard memlock unlimited
Use the remote connection tool MoBa to connect to the server, and use ulimit - a to view ulimit value, which is consistent with /etc/security/limits. Conf file configuration.
When using SSH command line remote connection, use ulimit - a to view ulimit value, which is the default value, which is inconsistent with /etc/security/limits. Conf file configuration.
When the operation and maintenance program starts the system remotely, it uses the SSH connection to execute in the past, and the ulimit value in the SSH connection does not take effect. As a result, the system cannot use RDMA because the default configuration of memlock is too small.
Investigation
After a series of investigation, we found that the SSH version of the customer environment (openssh)_ 4p1) and the default SSH version of the operating system (openssh)_ 7.4p1). It is suspected that the client’s recompiled version will cause the limit value of remote SSH login not to take effect
at the same time/etc/SSH/sshd_ The usepam value of the config file is No. when this item is configured to yes, restart the sshd server and view the system log. The error is as follows:
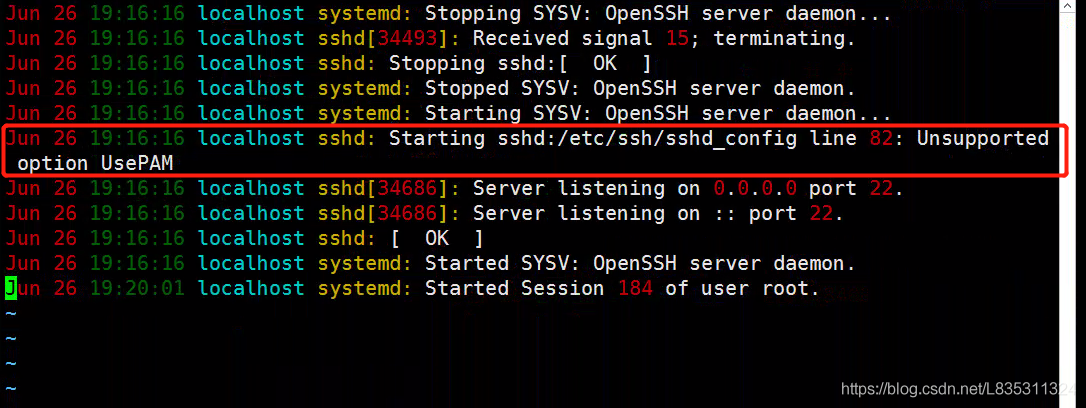
It is suspected that upgrading and compiling SSH to add – with PAM (this module is not compiled by default) will cause this problem.
solve
It is recommended that customers recompile the openssh version with the – with PAM parameter. Problem solving after customer operation.
Suggestions
The – with PAM parameter is required for the subsequent upgrade and compilation of openssh.
Expansion
Introduction of PAM module
Linux PAM (i.e. Linux pluggable authentication module) is a set of shared libraries, which enables local system administrators to choose the authentication mode of programs at will. In other words, you can change the authentication mechanism without recompiling an application with PAM function. In this way, even if you upgrade the local authentication mechanism, you don’t need to modify the program.
PAM uses the configuration file under/etc/pam.d/ to manage the authentication mode of the program. The application program calls the corresponding configuration file to call the local authentication module. The module is placed under/lib/security to load the dynamic library. For example, when we use the Su command, the system will prompt you to enter the password of the root user. This is what the Su command realizes by calling the PAM module.
SSH login will also refer to the modification module, and the configuration file is/etc/pam.d/sshd
#%PAM-1.0
auth required pam_sepermit.so
auth substack password-auth
auth include postlogin
# Used with polkit to reauthorize users in remote sessions
-auth optional pam_reauthorize.so prepare
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session required pam_namespace.so
session optional pam_keyinit.so force revoke
session include password-auth
session include postlogin
# Used with polkit to reauthorize users in remote sessions
-session optional pam_reauthorize.so prepare
The session section will include the password auth configuration, and the/etc/pam.d/password-auth-ac file is as follows:
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required pam_env.so
auth required pam_faildelay.so delay=2000000
auth sufficient pam_unix.so nullok try_first_pass
auth requisite pam_succeed_if.so uid >= 1000 quiet_success
auth required pam_deny.so
account required pam_unix.so
account sufficient pam_localuser.so
account sufficient pam_succeed_if.so uid < 1000 quiet
account required pam_permit.so
password requisite pam_pwquality.so try_first_pass local_users_only retry=3 authtok_type=
password sufficient pam_unix.so sha512 shadow nullok try_first_pass use_authtok
password required pam_deny.so
session optional pam_keyinit.so revoke
session required pam_limits.so
-session optional pam_systemd.so
session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
session required pam_unix.so
PAM_ Limits.so is the so module that will be called when creating an SSH connection, that is, the core so that the/etc/security/limits.conf file takes effect.
Reference documents
https://www.cnblogs.com/kevingrace/p/8671964.html